Cybersecurity Expert Outwits Deepfake Detector: CNN Business Report
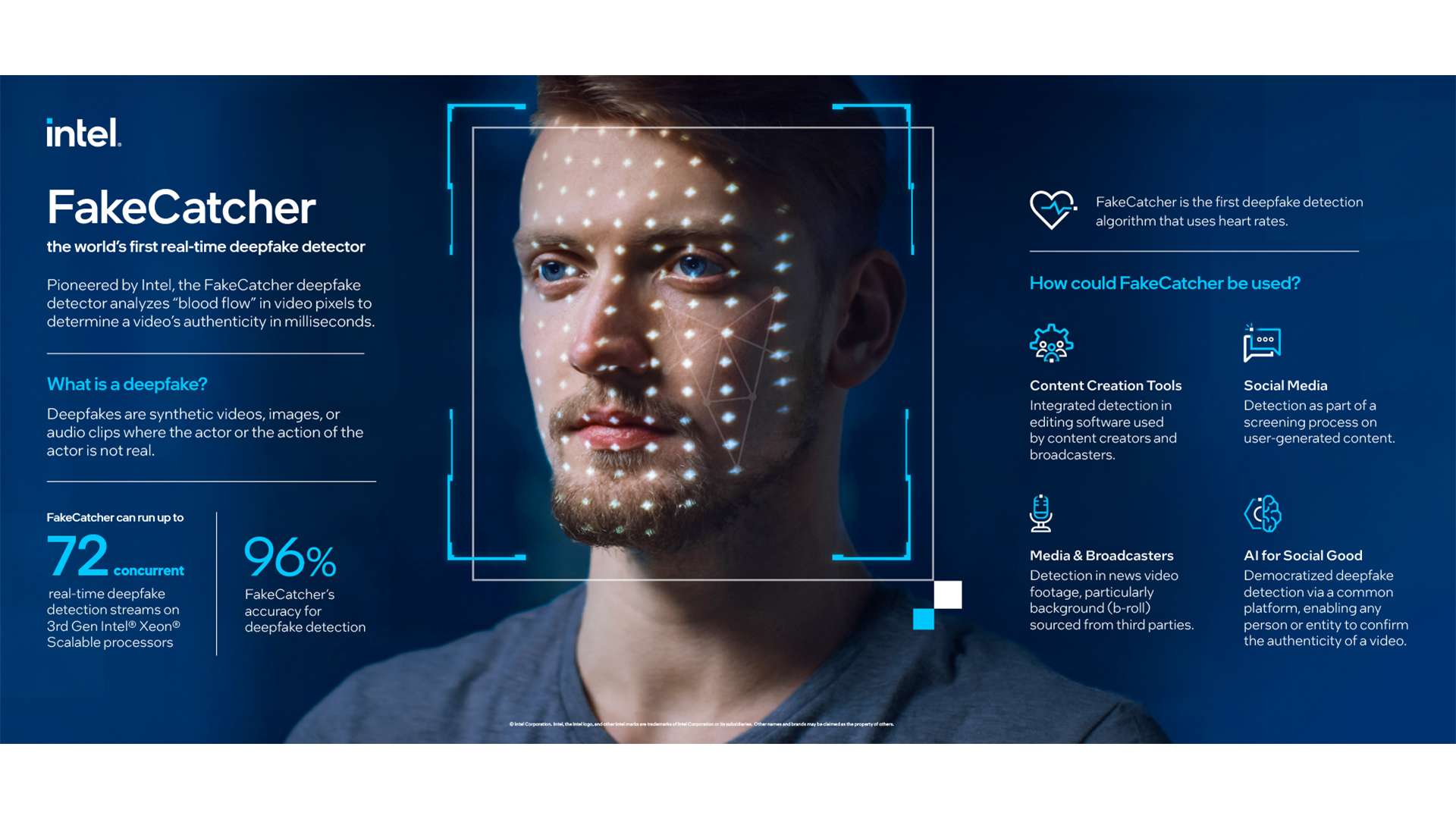
Table of Contents
The Expert's Methodology: Bypassing Deepfake Detection
Understanding the limitations of current deepfake detection algorithms.
Current deepfake detection algorithms rely on several methods to identify manipulated media. These include:
- Analyzing inconsistencies in eye blinking: Deepfakes often struggle to accurately replicate natural eye blinking patterns.
- Detecting subtle artifacts: Algorithms look for inconsistencies in image or video compression, pixel inconsistencies, or other subtle signs of manipulation.
- Analyzing inconsistencies in lighting and shadow: Discrepancies in lighting and shadow across a video can reveal a deepfake.
However, the cybersecurity expert in the CNN Business report exploited weaknesses in these techniques. The expert focused on a video-based deepfake, specifically targeting the limitations of algorithms in detecting subtle manipulations of lighting and shadow consistency.
The Expert's Innovative Approach: A Detailed Analysis.
The expert employed a sophisticated approach that can be described as an "adversarial attack." This involved:
- Targeted pixel manipulation: The expert didn't create a completely new video; instead, they subtly altered specific pixels to influence the detection algorithm's output, essentially creating a "camouflage" for the deepfake.
- Metadata manipulation: Minor alterations were made to the video's metadata, making it harder for detectors to flag it as potentially manipulated.
- Exploiting algorithm biases: The expert identified and leveraged biases within the specific deepfake detection algorithm used, effectively bypassing its detection mechanisms. This involved a deep understanding of the algorithm's internal workings and its vulnerabilities.
The expert's success highlights the limitations of relying on a single detection method and demonstrates the need for more adaptable and robust systems.
Implications for Deepfake Detection Technology and Online Security
The Vulnerability of Current Deepfake Detection Systems.
The success of the cybersecurity expert outwits deepfake detector experiment demonstrates several crucial vulnerabilities:
- Algorithm-specific weaknesses: What works against one algorithm may not work against another, highlighting the need for diverse and layered approaches.
- The arms race: As detection methods improve, so will the sophistication of deepfake creation techniques, creating a constant cycle of improvement and counter-improvement.
- Over-reliance on automation: Completely automated systems can be easily fooled. Human oversight and expert analysis are critical for confirming detection results.
Increased Risk of Misinformation and Online Fraud.
The ability to bypass deepfake detection systems has serious implications:
- Political manipulation: Deepfakes can be used to create fabricated evidence, spread misinformation, and damage reputations of political figures.
- Financial fraud: Deepfakes can be used for impersonation, leading to identity theft or fraudulent transactions.
- Social disruption: The widespread use of believable deepfakes can erode public trust and social cohesion. For instance, a recent deepfake scam involved a CEO being seemingly tricked into transferring funds based on a convincingly fake video call.
Future Directions in Deepfake Detection and Cybersecurity
The Need for Advanced Detection Methods.
Future solutions require a multi-faceted approach:
- Advanced AI countermeasures: Developing AI systems capable of identifying even subtle manipulations and adapting to new deepfake techniques.
- Blockchain technology integration: Using blockchain to create tamper-proof records of media authenticity.
- Improved data analysis techniques: Incorporating techniques from digital forensics to identify anomalies and trace the origin of media.
Collaboration and Education as Key Strategies.
Addressing the deepfake threat requires collaboration and education:
- Cross-industry collaboration: Cooperation between cybersecurity experts, technology developers, and law enforcement is essential to combat this threat effectively.
- Public awareness campaigns: Educating the public about deepfakes and how to identify potential manipulations.
- Media literacy programs: Developing critical thinking skills to help people evaluate the authenticity of online information.
Conclusion: Addressing the Challenges of Deepfake Detection
The CNN Business report's coverage of a cybersecurity expert outwitting deepfake detector highlights a critical vulnerability in current deepfake detection technology. The ability to bypass these systems poses significant threats to online security, increasing the risks of misinformation, fraud, and social instability. To combat this evolving threat, we need advanced detection methods, collaborative efforts between various stakeholders, and increased public awareness regarding the deceptive nature of deepfakes. Stay vigilant against the evolving threat of deepfakes. Learn more about deepfake detection techniques and best practices for online safety to protect yourself from the dangers highlighted in this CNN Business report on a cybersecurity expert outwitting deepfake detectors. [Link to relevant resource 1] [Link to relevant resource 2]

Featured Posts
-
 Angel Reeses Bold New Reebok Ss 25 Collection A First Look
May 17, 2025
Angel Reeses Bold New Reebok Ss 25 Collection A First Look
May 17, 2025 -
 Tuerkiye Birlesik Arap Emirlikleri Iliskilerinde Yeni Bir Doenem Erdogan Al Nahyan Goeruesmesi
May 17, 2025
Tuerkiye Birlesik Arap Emirlikleri Iliskilerinde Yeni Bir Doenem Erdogan Al Nahyan Goeruesmesi
May 17, 2025 -
 Did Lawrence O Donnell Expose Trumps Humiliation On Live Tv
May 17, 2025
Did Lawrence O Donnell Expose Trumps Humiliation On Live Tv
May 17, 2025 -
 Is Reddit Down In The Us Many Users Report Page Not Found Errors
May 17, 2025
Is Reddit Down In The Us Many Users Report Page Not Found Errors
May 17, 2025 -
 Hollywood At A Standstill The Writers And Actors Strike
May 17, 2025
Hollywood At A Standstill The Writers And Actors Strike
May 17, 2025
