Exec Office365 Breach: Crook Makes Millions, Feds Say
Table of Contents
The Scale of the Office365 Breach and Financial Losses
This significant Office365 breach resulted in the theft of millions of dollars, according to federal authorities. While the exact number of victims remains undisclosed for investigative reasons, the financial impact on affected businesses is substantial. Beyond the immediate loss of funds, companies face significant indirect costs:
- Lost Productivity: Employees spend valuable time dealing with the aftermath of the breach, including account recovery, security audits, and damage control.
- Reputational Damage: A data breach severely damages a company's reputation, leading to loss of customer trust and potential business opportunities.
- Legal Fees and Penalties: Businesses face substantial legal costs associated with investigations, compliance requirements, and potential lawsuits. Non-compliance with data protection regulations like GDPR can lead to hefty fines.
Specific examples of financial losses, as reported (where publicly available), include direct theft of funds from company accounts, fraudulent transactions, and the cost of remediation efforts. The long-term consequences could include decreased investor confidence and difficulty securing future funding. Official reports, once released publicly, will offer a more complete picture of the damage inflicted by this Office365 breach.
Methods Used in the Office365 Breach
The perpetrator employed sophisticated techniques to gain access to the Office365 accounts. The methods used illustrate the ever-evolving nature of cybercrime and the need for robust security protocols. Access was likely gained through a combination of:
- Phishing Attacks: Highly targeted phishing emails, perhaps mimicking legitimate communications from trusted sources, were used to trick employees into revealing their login credentials. These emails may have contained malicious links or attachments.
- Credential Stuffing: Stolen credentials from other breaches were likely used to attempt logins to Office365 accounts.
- Exploiting Vulnerabilities: Outdated software and unpatched vulnerabilities in the target systems could have been exploited to gain unauthorized access.
This wasn't a simple brute-force attack; the sophistication suggests a well-planned and executed campaign utilizing readily available tools and techniques. The perpetrator's detailed knowledge of Office365's security features highlights the necessity for ongoing training and awareness among employees.
The Role of Federal Authorities in the Investigation
Federal agencies, including the FBI (and potentially others depending on the jurisdiction), are actively involved in investigating this major Office365 breach. Their efforts involve:
- Tracing the Financial Trail: Tracking the movement of stolen funds to identify the perpetrator and their associates.
- Digital Forensics: Examining compromised systems and data to understand the attack methods and scope.
- International Cooperation: Collaborating with international law enforcement agencies if the perpetrator operates across borders.
The investigation timeline is ongoing. Charges against the individual responsible, once filed and proven in court, will provide a legal conclusion to the case. This illustrates the serious legal ramifications of such crimes and the resources governments invest in combating cybercrime.
Preventing Similar Office365 Breaches: Best Practices
Protecting your organization from a similar Office365 breach requires a multi-layered approach:
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, requiring users to provide multiple forms of authentication (e.g., password and a code from a mobile app) before accessing accounts.
- Employee Training: Regular security awareness training is crucial to educate employees about phishing attempts, social engineering tactics, and safe password practices. Simulations and phishing tests can help identify vulnerabilities in your workforce.
- Strong Password Management: Enforce strong, unique passwords for all accounts, and encourage the use of a password manager to simplify this process.
- Regular Security Updates: Ensure all software and systems are kept up to date with the latest security patches to mitigate known vulnerabilities.
- Security Audits and Vulnerability Assessments: Regular security audits and vulnerability assessments can identify weaknesses in your systems and help prioritize remediation efforts.
- Robust Cybersecurity Policies and Procedures: Establish clear and comprehensive cybersecurity policies and procedures, ensuring all employees understand their responsibilities.
By proactively implementing these measures, businesses can significantly reduce their risk of experiencing a devastating Office365 breach.
Conclusion: Learning from the Exec Office365 Breach
This Office365 breach serves as a stark reminder of the real financial and reputational risks associated with inadequate cybersecurity. The sophisticated methods employed underscore the need for a proactive, multi-faceted approach to security. Don't become the next victim of an Office365 breach; invest in robust security solutions, comprehensive employee training, and implement the best practices outlined above to secure your Office365 environment and prevent a costly and damaging incident. Proactive Office365 breach prevention is not an expense; it's an investment in the future of your business.

Featured Posts
-
 Neverovatna Pobeda Runea Nad Povredenim Alcarasom U Barseloni
May 17, 2025
Neverovatna Pobeda Runea Nad Povredenim Alcarasom U Barseloni
May 17, 2025 -
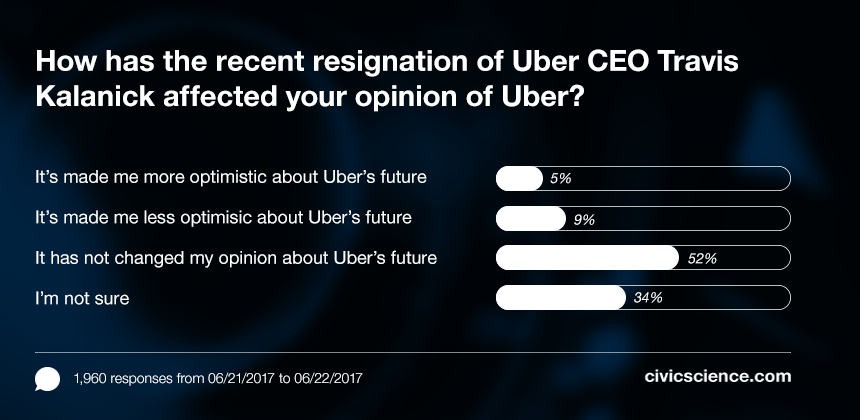 Former Uber Ceo Kalanick Reveals Regret Over Specific Project Strategy Decision
May 17, 2025
Former Uber Ceo Kalanick Reveals Regret Over Specific Project Strategy Decision
May 17, 2025 -
 Network18 Media And Investments Stock Price Charts Analysis 21 Apr 2025
May 17, 2025
Network18 Media And Investments Stock Price Charts Analysis 21 Apr 2025
May 17, 2025 -
 Generalka Kosarkaske Reprezentacije Srbije Pred Evrobasket Sve Vesti Iz Bajerne
May 17, 2025
Generalka Kosarkaske Reprezentacije Srbije Pred Evrobasket Sve Vesti Iz Bajerne
May 17, 2025 -
 Que Fue El Esquema Ponzi De Koriun Inversiones
May 17, 2025
Que Fue El Esquema Ponzi De Koriun Inversiones
May 17, 2025
