Federal Charges Filed Against Hacker Who Targeted Executive Office365 Accounts

Table of Contents
Details of the Cyberattack
The cyberattack, believed to have been orchestrated over several months, utilized a combination of sophisticated phishing techniques and malware to gain unauthorized access to multiple Executive Office 365 accounts. The targets were specifically chosen high-ranking executives within several Fortune 500 companies, suggesting a deliberate and targeted campaign aimed at accessing sensitive company information. The scale of the breach is still being assessed, but initial investigations suggest that hundreds of accounts were compromised.
- The attacker gained access through spear-phishing emails designed to mimic legitimate communications. These emails contained malicious attachments or links that downloaded malware onto the victims' computers.
- Once inside the network, the attacker moved laterally, gaining access to sensitive data including financial projections, confidential merger and acquisition documents, and intellectual property.
- The breach exposed not only sensitive company data but also personal information of employees, including social security numbers and addresses, potentially leading to identity theft.
- Access to sensitive financial reports.
- Exposure of confidential client information.
- Compromise of strategic planning documents.
The Accused Hacker and Their Methods
While the full identity of the accused hacker remains partially sealed under court order pending further investigation, court documents reveal the suspect used advanced techniques, indicating potential ties to organized cybercrime. The individual allegedly utilized custom-built malware and exploited known vulnerabilities in Microsoft's Office 365 platform, demonstrating a high level of technical expertise. The suspect's methods show clear evidence of meticulous planning and execution.
- Law enforcement agencies traced the origin of malicious emails back to a server located in a foreign country.
- Investigators employed advanced forensic techniques to analyze the malware and identify the attacker's methods.
- Collaboration between federal agencies and private cybersecurity firms played a crucial role in the apprehension of the suspect.
- Tracing the source of malicious emails.
- Investigation of suspicious network activity.
Federal Charges and Potential Penalties
The hacker faces multiple federal charges, including unauthorized access to computer systems, wire fraud, and aggravated identity theft. The gravity of these charges carries severe penalties, including significant prison time—potentially up to 20 years—and substantial fines. The impact on the hacker's future career and reputation is likely to be devastating. Furthermore, civil lawsuits from affected parties could add to the already substantial penalties.
- Sentencing guidelines for similar offenses suggest a lengthy prison sentence.
- Potential for civil lawsuits from affected parties could result in millions of dollars in damages.
- The conviction would severely hamper the individual’s ability to find employment in the IT field in the future.
Lessons Learned and Security Recommendations
This Executive Office 365 account hack serves as a stark reminder of the ever-evolving threats in the digital landscape. Organizations must adopt a proactive approach to cybersecurity to mitigate the risk of similar attacks. Strengthening security measures should be a top priority.
- Implement multi-factor authentication (MFA) for all Office 365 accounts, adding an extra layer of security beyond passwords.
- Conduct regular security awareness training for employees to educate them about phishing scams and other social engineering tactics.
- Enforce strong and unique passwords for all accounts, and encourage the use of password managers.
- Keep all software and systems updated with the latest security patches.
- Regular security audits and penetration testing are essential to identify vulnerabilities before attackers can exploit them.
Conclusion
The severity of this Executive Office 365 account hack cannot be overstated. The resulting federal charges against the perpetrator underscore the seriousness of these crimes and the potential consequences for those involved. Organizations must learn from this incident and prioritize proactive cybersecurity measures. Regular security reviews, employee training, and the implementation of robust security protocols, including multi-factor authentication, are crucial to prevent future Executive Office 365 account hacks and protect valuable data. Review your organization's security protocols today and take steps to strengthen your defenses against sophisticated cyber threats. For further information on securing your Office 365 environment, explore resources from Microsoft and leading cybersecurity firms.

Featured Posts
-
 Glastonbury 2024 Liverpool Band Rumoured For Secret Set
May 30, 2025
Glastonbury 2024 Liverpool Band Rumoured For Secret Set
May 30, 2025 -
 Le Pen Les Lois Et L Interpretation De Jacobelli Decryptage
May 30, 2025
Le Pen Les Lois Et L Interpretation De Jacobelli Decryptage
May 30, 2025 -
 Transfercoup Augsburg Holt Torwart Garteig Von Ingolstadt
May 30, 2025
Transfercoup Augsburg Holt Torwart Garteig Von Ingolstadt
May 30, 2025 -
 Ticketmaster Ofrece Mayor Transparencia En El Precio De Sus Boletos
May 30, 2025
Ticketmaster Ofrece Mayor Transparencia En El Precio De Sus Boletos
May 30, 2025 -
 Augsburg Schnappt Sich Garteig Ingolstadt Torwart Wechselt Zum Fca
May 30, 2025
Augsburg Schnappt Sich Garteig Ingolstadt Torwart Wechselt Zum Fca
May 30, 2025
Latest Posts
-
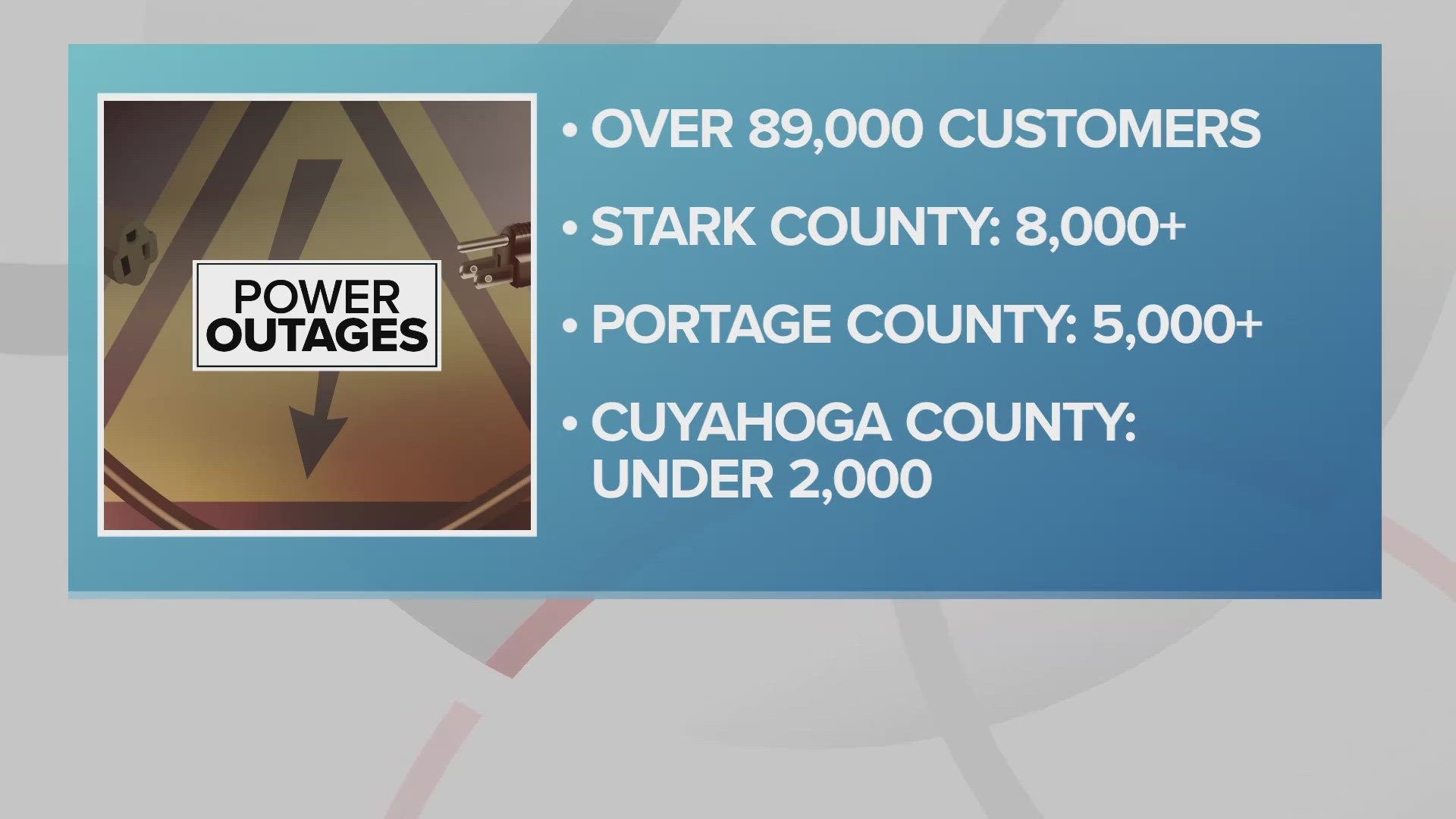 Severe Thunderstorms Bring Power Outages To Northeast Ohio Stay Safe And Informed
May 31, 2025
Severe Thunderstorms Bring Power Outages To Northeast Ohio Stay Safe And Informed
May 31, 2025 -
 Power Outages And Weather Alerts Issued Across Northeast Ohio Due To Intense Thunderstorms
May 31, 2025
Power Outages And Weather Alerts Issued Across Northeast Ohio Due To Intense Thunderstorms
May 31, 2025 -
 April 29th Twins Guardians Game Progressive Field Weather And Potential Delays
May 31, 2025
April 29th Twins Guardians Game Progressive Field Weather And Potential Delays
May 31, 2025 -
 Rain Possible On Election Day In Northeast Ohio
May 31, 2025
Rain Possible On Election Day In Northeast Ohio
May 31, 2025 -
 Cleveland Fire Station Temporary Closure After Significant Water Leaks
May 31, 2025
Cleveland Fire Station Temporary Closure After Significant Water Leaks
May 31, 2025
