Federal Charges: Millions Stolen Via Office365 Executive Account Hacks
Table of Contents
The Scale of the Heist and the Victims Involved
The sheer scale of the financial theft is alarming. Authorities estimate that over $5 million was stolen from a diverse range of businesses, impacting both large multinational corporations and smaller government entities. The attackers displayed a clear preference for targeting executive-level accounts, gaining access to sensitive financial data and internal systems.
-
Specific examples: While specifics are currently under seal to protect the ongoing investigation, anonymized case studies reveal a pattern of targeting companies in the finance, technology, and healthcare sectors. One case involved the theft of sensitive merger and acquisition data, resulting in significant financial losses and reputational damage. Another involved the fraudulent transfer of funds from corporate accounts.
-
Long-term consequences: The aftermath of such a cybersecurity breach extends far beyond the immediate financial loss. Victims face protracted legal battles, significant reputational damage, loss of investor confidence, and potential regulatory fines. The cost of recovering from a data breach, including legal fees, forensic investigations, and reputational repair, can far exceed the initial financial losses. Keywords: Cybersecurity breach, financial fraud, data loss, corporate espionage.
The Methods Used in the Office365 Executive Account Hacks
The attackers employed a multi-pronged approach, combining several sophisticated techniques to breach Office365 executive accounts. This wasn't a simple phishing attempt; it was a carefully orchestrated campaign leveraging advanced attack vectors.
-
Spear phishing and credential stuffing: The primary method involved highly targeted spear-phishing campaigns disguised as legitimate business communications. These emails contained malicious links or attachments designed to install malware or harvest login credentials. Credential stuffing – using stolen usernames and passwords from other data breaches to access accounts – was also employed.
-
Exploiting zero-day vulnerabilities: Evidence suggests the attackers may have exploited previously unknown vulnerabilities (zero-day exploits) in Office365 itself or related third-party applications. This highlights the constant arms race between attackers and security providers.
-
Multi-factor authentication (MFA) bypass: While MFA is a critical security layer, the attackers likely bypassed it using sophisticated techniques, potentially involving social engineering or exploiting vulnerabilities in MFA implementation. This underscores the importance of not only implementing MFA, but also ensuring its proper configuration and user training. Keywords: Phishing attacks, credential stuffing, spear phishing, malware, zero-day exploits, multi-factor authentication bypass.
The Federal Charges and Potential Penalties
The perpetrators face multiple federal charges, including wire fraud, identity theft, and computer fraud, all carrying significant penalties. The Department of Justice is pursuing aggressive prosecution, highlighting the severity of these crimes.
-
Specific charges: The indictment details specific instances of fraudulent wire transfers, unauthorized access to protected computer systems, and identity theft used to facilitate the fraudulent activities.
-
Potential penalties: The defendants face decades in prison and millions of dollars in fines. The ongoing investigation continues, and further charges are possible. The severity of the sentencing reflects the escalating consequences of cybercrime at the federal level. Keywords: Wire fraud, identity theft, computer crime, federal prosecution, sentencing guidelines.
Lessons Learned and Best Practices for Preventing Office365 Executive Account Hacks
This case underscores the urgent need for businesses to bolster their cybersecurity defenses. The following best practices are essential to mitigate the risk of similar attacks.
-
Robust multi-factor authentication (MFA): Implementing MFA across all accounts, especially executive-level accounts, is paramount. Consider using a combination of methods, such as password managers and authenticator apps.
-
Strong password policies and management: Enforce strong, unique passwords for all accounts and encourage the use of password managers to simplify management.
-
Comprehensive security awareness training: Regular employee training is crucial to educate staff on phishing scams, social engineering tactics, and other cybersecurity threats.
-
Regular security audits and penetration testing: Regularly assess your security posture through penetration testing and vulnerability scans to identify weaknesses before attackers can exploit them.
-
Advanced threat protection: Implement advanced threat protection solutions to detect and prevent malicious activity, including behavior-based analysis and machine learning.
-
Security Information and Event Management (SIEM) systems: Utilize SIEM systems to monitor security events, correlate data from multiple sources, and detect suspicious activity.
-
Incident response plan: Develop and regularly test a comprehensive incident response plan to mitigate the impact of a successful attack. Keywords: Multi-factor authentication (MFA), password management, security awareness training, cybersecurity best practices, threat intelligence, incident response plan.
Conclusion
The recent federal charges stemming from millions stolen through Office365 executive account hacks serve as a stark warning of the ever-evolving landscape of cybercrime. The sophistication of the attacks, the significant financial losses, and the potential for long-term reputational damage highlight the critical need for proactive cybersecurity measures. Implementing robust multi-factor authentication, rigorous security awareness training, and advanced threat protection solutions are no longer optional but essential for protecting your organization from Office365 executive account hacks and other sophisticated cyber threats. Don't wait for a similar incident to befall your business; take action now. Consult with a cybersecurity professional to assess your vulnerability and implement the appropriate safeguards. Protecting your organization from these threats is an ongoing process, requiring constant vigilance and adaptation.

Featured Posts
-
 Taylor Swift Albums Ranked From Debut To Midnights
May 18, 2025
Taylor Swift Albums Ranked From Debut To Midnights
May 18, 2025 -
 Analyzing Indias Reduced Engagement With Pakistan Turkey And Azerbaijan
May 18, 2025
Analyzing Indias Reduced Engagement With Pakistan Turkey And Azerbaijan
May 18, 2025 -
 Did Julia Fox Copy Bianca Censori Kanye Wests Ex Under Fire For Risque Look
May 18, 2025
Did Julia Fox Copy Bianca Censori Kanye Wests Ex Under Fire For Risque Look
May 18, 2025 -
 Navigating Metropolis Japan A Practical Travel Guide
May 18, 2025
Navigating Metropolis Japan A Practical Travel Guide
May 18, 2025 -
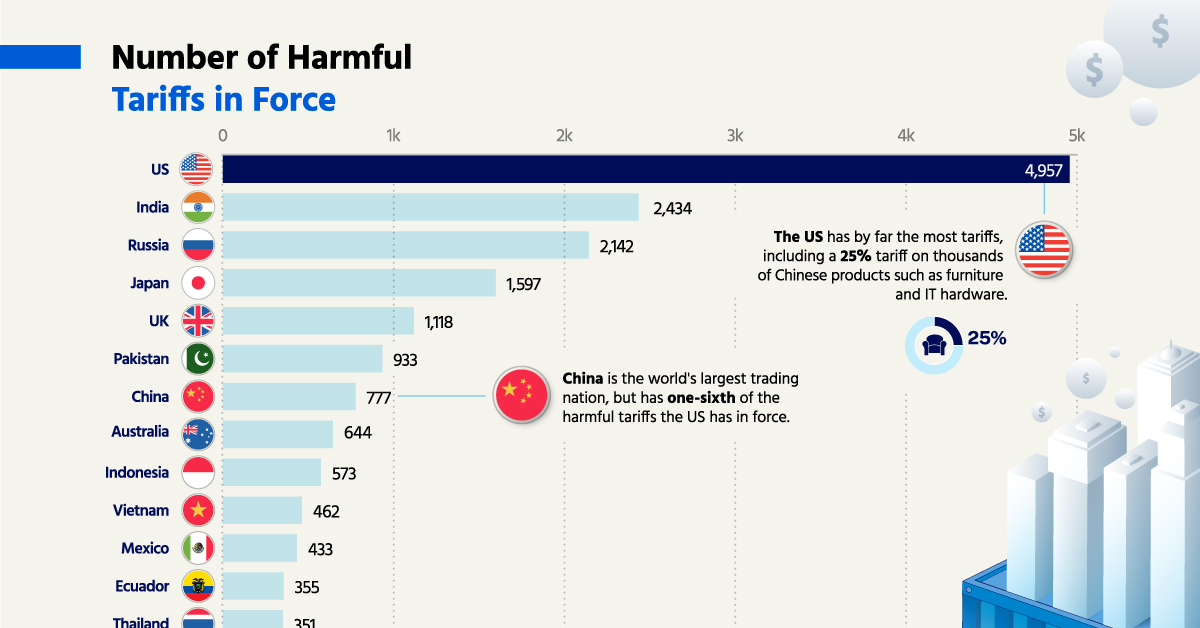 Southwest Washingtons Economy Navigating The New Tariff Landscape
May 18, 2025
Southwest Washingtons Economy Navigating The New Tariff Landscape
May 18, 2025
Latest Posts
-
 The Swim With Mike Program A Lifeline For Trojans
May 18, 2025
The Swim With Mike Program A Lifeline For Trojans
May 18, 2025 -
 Swim With Mike Program Fosters Community Among Trojans
May 18, 2025
Swim With Mike Program Fosters Community Among Trojans
May 18, 2025 -
 Finding Community How Swim With Mike Helps Trojans
May 18, 2025
Finding Community How Swim With Mike Helps Trojans
May 18, 2025 -
 Swim With Mike Building Community For Trojans
May 18, 2025
Swim With Mike Building Community For Trojans
May 18, 2025 -
 Mikey Madisons Snl Cold Open A Signal Group Chat Spoof
May 18, 2025
Mikey Madisons Snl Cold Open A Signal Group Chat Spoof
May 18, 2025
