Millions Lost: Insider Threat Or Sophisticated Office365 Hack?
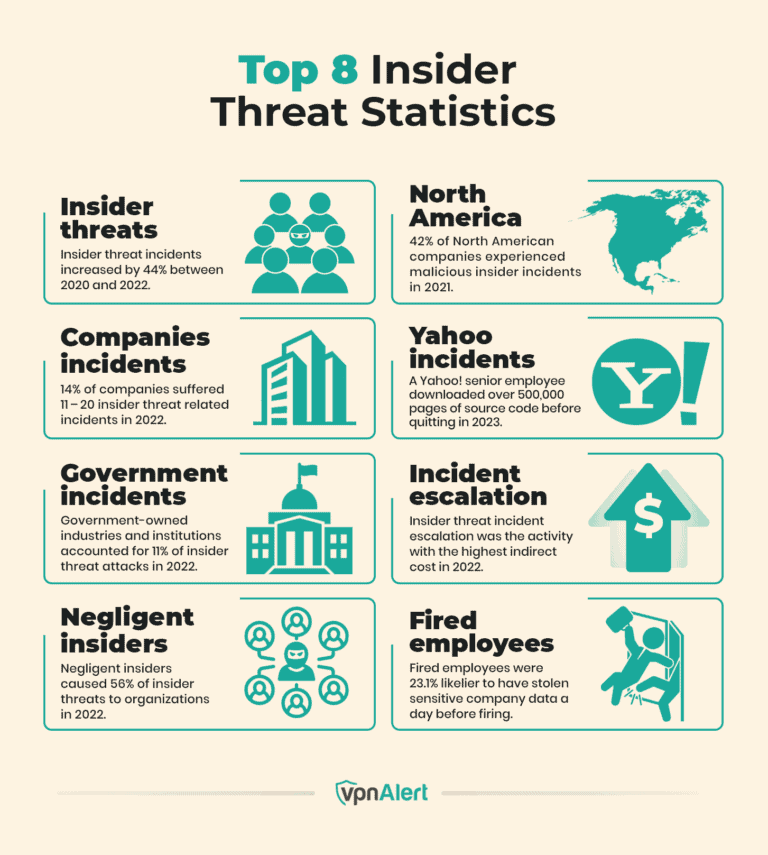
Table of Contents
The Insider Threat: A Wolf in Sheep's Clothing
Insider threats, those originating from within the organization, can be devastating. A trusted employee, contractor, or even a former employee with lingering access can inflict significant damage. Identifying these threats requires vigilance and a proactive security approach.
Identifying Red Flags of Insider Malfeasance:
Detecting an insider threat often relies on identifying unusual patterns in user behavior. Look for these red flags:
- Unusual access patterns outside normal working hours: Access attempts late at night or on weekends, especially involving sensitive data, warrant investigation.
- Data exfiltration attempts masked as legitimate activity: Large data transfers disguised as routine backups or reports can indicate malicious intent.
- Changes in user behavior: A sudden increase in access requests to sensitive data or areas of the network the employee typically doesn't need to access is a warning sign.
- Suspicious communication with external parties: Unusual communication patterns, especially with known malicious actors or competitors, should trigger an alarm.
- Unexplained privileges or access granted to accounts: Unusual changes in user permissions or the granting of excessive privileges to accounts without a legitimate business reason are highly suspicious.
Motivations Behind Insider Threats:
Understanding the motivations behind insider threats can inform preventive measures. Common motivations include:
- Financial gain: Selling stolen data on the dark web for profit.
- Revenge or retribution: An employee disgruntled by the organization may seek to cause damage.
- Ideological reasons: Whistleblowing or leaking confidential information for political or social causes.
- Negligence or lack of awareness: An employee might unintentionally compromise security due to a lack of training or awareness of security protocols.
Mitigating Insider Threats:
A multi-layered approach is crucial to mitigate the risk of insider threats:
- Implement robust access control and privilege management: Employ the principle of least privilege, granting users only the access they need to perform their jobs.
- Conduct regular security awareness training for employees: Educate employees about phishing scams, social engineering tactics, and the importance of data security.
- Monitor user activity for suspicious patterns using security information and event management (SIEM) tools: These tools can analyze logs and detect anomalies indicating malicious activity.
- Establish clear data governance policies and procedures: Define clear rules regarding data access, usage, and protection, and ensure employees understand and adhere to these policies.
The Sophisticated Office365 Hack: Advanced Persistent Threats (APTs)
External attackers employing advanced techniques pose a significant threat to Office365 environments. These sophisticated Office365 hacks often involve Advanced Persistent Threats (APTs), which can remain undetected for extended periods.
Common Tactics Used in Office365 Attacks:
APTs utilize various tactics to compromise Office365 accounts and data:
- Phishing campaigns targeting employee credentials: Malicious emails designed to trick employees into revealing their login credentials.
- Exploiting vulnerabilities in Office365 applications: Attackers may exploit known vulnerabilities in Office365 applications or services.
- Using compromised accounts to gain access to sensitive data: Once an account is compromised, attackers can access and exfiltrate sensitive data.
- Leveraging social engineering techniques: Manipulating employees through psychological tactics to gain access or information.
- Deploying malware to steal data and maintain persistence: Malware can be used to steal data, maintain access to the system, and hinder detection.
Recognizing Signs of a Sophisticated Hack:
Identifying a sophisticated Office365 hack requires careful monitoring and analysis:
- Unusual login attempts from unfamiliar locations: Logins from unexpected geographical locations indicate potential compromise.
- Unexplained changes to system configurations: Unexpected changes to system settings or policies can signal malicious activity.
- Detection of malware or suspicious processes: Antivirus and endpoint detection and response (EDR) tools can identify malicious software.
- Data breaches impacting a large number of accounts: A widespread breach indicates a sophisticated attack targeting the entire system.
- Compromised administrative accounts: Compromise of privileged accounts grants attackers extensive control over the system.
Protecting Against Advanced Office365 Hacks:
Robust security measures are crucial to defend against sophisticated Office365 hacks:
- Implement multi-factor authentication (MFA) for all accounts: MFA adds an extra layer of security, making it much harder for attackers to gain access.
- Keep software updated and patched: Regularly update Office365 applications and operating systems to patch known vulnerabilities.
- Utilize advanced threat protection features offered by Office365: Leverage Office 365's built-in security features, such as advanced threat protection and data loss prevention (DLP).
- Regularly review security logs and alerts: Monitor security logs for suspicious activity and promptly investigate any alerts.
- Conduct penetration testing and vulnerability assessments: Regularly test your Office365 environment to identify and address vulnerabilities before attackers can exploit them.
Differentiating Between Insider Threats and External Hacks
Distinguishing between insider threats and sophisticated external hacks can be challenging. Some attack vectors and indicators may overlap. For example, data exfiltration can occur in both scenarios. Thorough investigation and forensic analysis, including log reviews and network traffic analysis, are crucial to determine the source of a breach. This often requires engaging cybersecurity experts specializing in incident response and digital forensics.
Conclusion
Protecting your organization from devastating Office365 breaches requires a comprehensive approach that addresses both insider threats and sophisticated external hacks. Understanding the distinct characteristics of each threat vector is critical for developing effective preventive and detection strategies. By implementing robust access controls, conducting regular security awareness training, utilizing advanced threat protection tools, and maintaining a vigilant security posture, you can significantly reduce your risk of an Office365 hack and protect your valuable data. Don't wait for a breach to occur – assess your Office365 security posture today and take proactive steps to secure your organization. Invest in comprehensive Office365 security solutions and incident response planning to safeguard your business from the financial and reputational damage of a data breach. Protect your organization from devastating Office365 breaches – implement robust security measures today!

Featured Posts
-
 Le Travail Des Cordistes Face Au Developpement Vertical De Nantes
May 22, 2025
Le Travail Des Cordistes Face Au Developpement Vertical De Nantes
May 22, 2025 -
 31 Pay Cut For Bps Chief Executive Officer
May 22, 2025
31 Pay Cut For Bps Chief Executive Officer
May 22, 2025 -
 The Pig Familys Gender Reveal A Celebration For A New Arrival
May 22, 2025
The Pig Familys Gender Reveal A Celebration For A New Arrival
May 22, 2025 -
 600 Year Old Chinese Tower Partially Collapses Tourists Flee
May 22, 2025
600 Year Old Chinese Tower Partially Collapses Tourists Flee
May 22, 2025 -
 Thames Water Executive Bonuses A Case Study In Corporate Governance Failure
May 22, 2025
Thames Water Executive Bonuses A Case Study In Corporate Governance Failure
May 22, 2025
Latest Posts
-
 Recent Gas Price Increase Up Almost 20 Cents Per Gallon
May 22, 2025
Recent Gas Price Increase Up Almost 20 Cents Per Gallon
May 22, 2025 -
 Fuel Costs Soar A 20 Cent Per Gallon Increase
May 22, 2025
Fuel Costs Soar A 20 Cent Per Gallon Increase
May 22, 2025 -
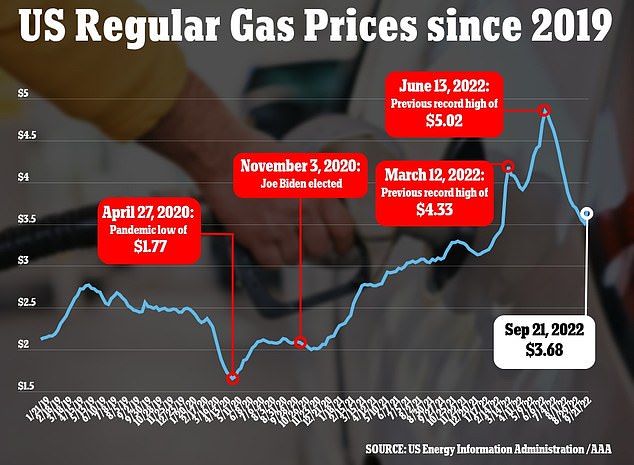 20 Cent Increase In Average Gas Prices Nationwide
May 22, 2025
20 Cent Increase In Average Gas Prices Nationwide
May 22, 2025 -
 Columbus Gas Prices 2 83 To 3 31 Per Gallon
May 22, 2025
Columbus Gas Prices 2 83 To 3 31 Per Gallon
May 22, 2025 -
 Gasoline Prices Surge In The Mid Hudson Valley
May 22, 2025
Gasoline Prices Surge In The Mid Hudson Valley
May 22, 2025
