Office 365 Exec Inboxes Targeted: Millions Made In Cybercrime, Feds Say
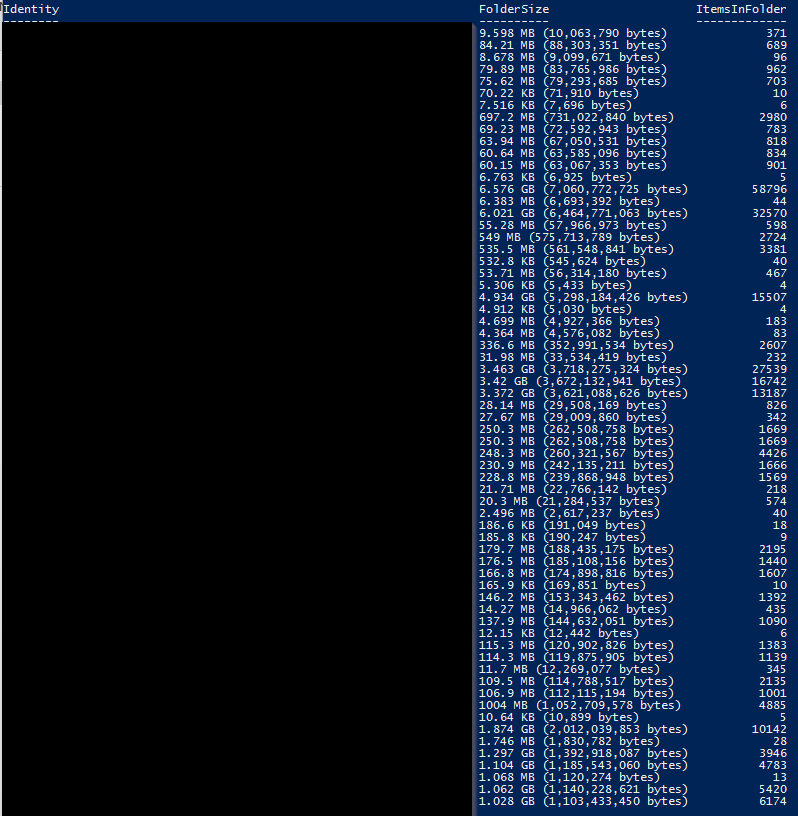
Table of Contents
The Tactics Behind Office 365 Executive Inbox Compromises
Cybercriminals employ various tactics to breach Office 365 executive inboxes. Understanding these methods is the first step towards effective prevention.
Phishing and Spear Phishing Attacks
Highly targeted phishing emails are a primary vector for Office 365 executive inbox compromise. These attacks impersonate trusted sources, such as CEOs, board members, or even IT departments, to trick executives into revealing sensitive information or clicking malicious links.
- Effectiveness: The success of these attacks relies on social engineering. Criminals craft believable emails tailored to the recipient's role and knowledge, making them difficult to distinguish from legitimate communications.
- Malicious Links and Attachments: Phishing emails often contain malicious links redirecting to fake login pages or downloading malware. Attachments, such as malicious documents (.doc, .docx, .xls, .xlsx), .zip files, or executable files (.exe), can also deliver malware to the victim's system.
- AI-Powered Personalization: The sophistication of these attacks is constantly increasing. Cybercriminals are leveraging AI-powered tools to personalize phishing emails, making them even harder to detect.
Examples:
- Subject lines: "Urgent Payment Request," "Confidential Board Meeting Documents," "Security Alert."
- Attachment types: Malicious documents (maldoc), .zip files containing malware, .exe files.
- Social engineering tactics: Creating a sense of urgency, exploiting trust relationships, leveraging fear of consequences.
Credential Stuffing and Brute-Force Attacks
Hackers also attempt to gain access to Office 365 executive inboxes using stolen credentials obtained from other data breaches (credential stuffing) or by trying numerous password combinations (brute-force attacks).
- Credential Stuffing: Attackers use lists of usernames and passwords leaked from other compromised systems to attempt logins on Office 365 accounts.
- Brute-Force Attacks: Automated tools are employed to systematically try various password combinations until a successful login is achieved.
Examples:
- Common password weaknesses exploited: Simple passwords, easily guessable information, reused passwords across multiple accounts.
- Importance of Multi-Factor Authentication (MFA): MFA significantly increases the security of accounts by requiring multiple forms of authentication, making brute-force and credential stuffing attacks much more difficult.
Exploiting Vulnerabilities in Third-Party Apps
Attackers can exploit vulnerabilities in third-party applications integrated with Office 365 to gain unauthorized access to executive inboxes.
- Weak Security in Third-Party Apps: Poorly secured third-party apps can act as entry points for hackers.
- Unauthorized Access: A compromised third-party app may grant attackers access to sensitive data, including emails and attachments.
Examples:
- Best practices for vetting and managing third-party apps: Thorough security assessments, regular audits, strong access control policies.
- Importance of regular security audits: Regularly assessing the security posture of third-party apps is vital to identify and mitigate potential vulnerabilities.
The Devastating Consequences of Office 365 Executive Inbox Breaches
The consequences of an Office 365 executive inbox compromise can be severe and far-reaching.
Financial Losses
These attacks lead to significant financial losses for organizations.
- Quantifiable Impact: Recent reports indicate millions of dollars lost due to fraudulent transactions initiated through compromised executive accounts.
- Remediation Costs: The costs associated with investigation, remediation, legal fees, and reputational damage can be substantial.
Examples:
- Fraudulent transactions: Wire transfer scams, unauthorized payments to vendors, fake invoices.
Reputational Damage
A breach can severely damage a company's reputation and erode public trust.
- Impact on Brand: Negative media coverage and loss of customer confidence can significantly impact brand value.
- Investor Confidence: Investors may lose confidence in the company, leading to decreased stock value.
Examples:
- Negative media coverage: News reports highlighting the security breach and the financial losses.
- Loss of clients: Clients may switch to competitors due to concerns about security.
Legal and Regulatory Compliance Issues
Data breaches can result in significant legal and regulatory repercussions.
- Legal Ramifications: Organizations face potential fines and lawsuits for non-compliance with data protection regulations.
- Regulatory Compliance: Compliance with regulations such as GDPR and CCPA is crucial to avoid hefty penalties.
Examples:
- Key regulations: GDPR, CCPA, HIPAA.
- Potential penalties: Significant fines, legal action, reputational damage.
Protecting Your Office 365 Executive Inboxes
Protecting against Office 365 executive inbox compromise requires a multi-layered approach.
Implementing Strong Authentication Methods
Strong authentication is crucial in preventing unauthorized access.
- Multi-Factor Authentication (MFA): Implement MFA for all user accounts, requiring multiple forms of authentication (password, OTP, biometric).
- Password Management: Enforce strong password policies and encourage employees to use password managers.
Examples:
- Different MFA options: One-time passwords (OTP), biometric authentication, security keys.
- Best practices for password management: Use unique and complex passwords, change passwords regularly, avoid using personal information in passwords.
Security Awareness Training
Educating employees is vital in preventing phishing attacks.
- Phishing Awareness: Train employees to identify and report suspicious emails.
- Social Engineering: Educate employees about social engineering tactics used by attackers.
Examples:
- Key topics to cover in security awareness training: Phishing, social engineering, malware, safe browsing practices.
- Frequency of training sessions: Regular refresher training sessions are recommended.
Regular Security Audits and Monitoring
Proactive monitoring and regular security assessments are essential.
- Vulnerability Identification: Regular security audits help identify and mitigate vulnerabilities.
- Suspicious Activity: Monitor user activity and detect suspicious behavior promptly.
Examples:
- Tools and techniques for security monitoring: Security Information and Event Management (SIEM) systems, intrusion detection systems (IDS).
- Importance of incident response planning: Develop and test an incident response plan to quickly contain and mitigate security breaches.
Conclusion
The targeting of Office 365 executive inboxes is a significant and growing threat. The financial losses, reputational damage, and legal liabilities are substantial. However, by implementing robust security measures, including strong authentication, comprehensive security awareness training, and proactive monitoring, organizations can significantly reduce their risk of Office 365 executive inbox compromise. Don't wait until it's too late. Protect your organization today. Implement a comprehensive security strategy and safeguard your executive leadership from the devastating consequences of these attacks. Invest in your security now – it's an investment in your future.

Featured Posts
-
 Moodys Downgrade Impact On Dow Futures And The Us Dollar
May 21, 2025
Moodys Downgrade Impact On Dow Futures And The Us Dollar
May 21, 2025 -
 Self Guided Walking Holiday In Provence Mountains To Mediterranean
May 21, 2025
Self Guided Walking Holiday In Provence Mountains To Mediterranean
May 21, 2025 -
 How Climate Risk Affects Your Mortgage Approval And Credit Score
May 21, 2025
How Climate Risk Affects Your Mortgage Approval And Credit Score
May 21, 2025 -
 Defi Loire Atlantique Quiz Histoire Gastronomie Et Culture
May 21, 2025
Defi Loire Atlantique Quiz Histoire Gastronomie Et Culture
May 21, 2025 -
 Solve The Nyt Mini Crossword March 5 2025 Hints And Solutions
May 21, 2025
Solve The Nyt Mini Crossword March 5 2025 Hints And Solutions
May 21, 2025
Latest Posts
-
 Preparing For A Wintry Mix Of Rain And Snow
May 21, 2025
Preparing For A Wintry Mix Of Rain And Snow
May 21, 2025 -
 Preparing For Drier Weather A Practical Guide
May 21, 2025
Preparing For Drier Weather A Practical Guide
May 21, 2025 -
 Wintry Mix Of Rain And Snow What To Expect
May 21, 2025
Wintry Mix Of Rain And Snow What To Expect
May 21, 2025 -
 When Will It Rain Precise Timing And Chances Of Precipitation
May 21, 2025
When Will It Rain Precise Timing And Chances Of Precipitation
May 21, 2025 -
 Checking For Rain Get The Latest Timing And Forecast Updates
May 21, 2025
Checking For Rain Get The Latest Timing And Forecast Updates
May 21, 2025
