Office 365 Security Breach: How A Crook Made Millions Targeting Executives

Table of Contents
This article delves into a real-world case study of a devastating Office 365 security breach that resulted in millions of dollars being stolen from unsuspecting executives. We'll examine the methods used, the vulnerabilities exploited, and the crucial lessons learned to help protect your organization from similar attacks. The sophisticated nature of this attack highlights the critical need for robust Office 365 security measures and proactive cybersecurity strategies.
The Sophisticated Phishing Campaign
The success of this multi-million dollar fraud hinged on a highly sophisticated phishing campaign targeting high-level executives. The attackers didn't rely on simple, easily detectable phishing emails; instead, they employed advanced techniques to bypass security measures and gain access to sensitive information.
Exploiting Known Vulnerabilities
The attackers cleverly leveraged several known vulnerabilities in the victim's Office 365 environment. This highlights the critical importance of regularly patching systems and updating security protocols.
- Weak Passwords: Many executives used easily guessable passwords or reused passwords across multiple platforms. This provided an easy entry point for the attackers.
- Lack of Multi-Factor Authentication (MFA): The absence of MFA allowed attackers to gain access even with stolen credentials. MFA adds an extra layer of security that significantly reduces the risk of unauthorized access.
- Inadequate Security Awareness Training: A lack of comprehensive security awareness training left executives vulnerable to sophisticated phishing tactics. Employees were not equipped to identify and report suspicious emails.
The attackers exploited these vulnerabilities by using credential stuffing attacks, attempting known username/password combinations obtained from previous data breaches on other platforms. Once a successful login was achieved, the attackers had access to the victim's Office 365 account.
Impersonation and Social Engineering
Beyond exploiting technical vulnerabilities, the attackers employed sophisticated social engineering techniques. They successfully impersonated trusted individuals and organizations to manipulate their victims into revealing sensitive information or performing actions that compromised security.
- Spoofing Email Addresses: Attackers created emails that appeared to originate from legitimate sources, such as the CEO's personal assistant or a trusted business partner. These emails were meticulously crafted to mimic genuine communication.
- Using Similar Domain Names: Attackers registered domain names very similar to legitimate company domains to create a sense of trust and authenticity. This subtle difference is often overlooked by unsuspecting users.
The psychology of social engineering played a crucial role. The attackers leveraged the urgency and authority implied in their communications, creating a sense of pressure that encouraged victims to act quickly without verifying the legitimacy of the requests. This resulted in the successful execution of their malicious plan.
The Data Breach and Financial Loss
Once the attackers gained access to the executive's Office 365 accounts, they swiftly moved to access and exploit sensitive financial information.
Accessing Sensitive Financial Information
The compromised accounts provided the attackers with a wealth of sensitive data, enabling them to execute their financial fraud scheme.
- Bank Account Details: The attackers gained access to bank account numbers, routing numbers, and other crucial financial information.
- Wire Transfer Instructions: They obtained wire transfer instructions, allowing them to redirect funds to accounts controlled by them.
- Financial Reports: Access to financial reports allowed them to identify the most lucrative targets and plan their attacks accordingly.
The attackers meticulously used this information to execute fraudulent wire transfers, diverting millions of dollars from the victim companies to offshore accounts.
The Financial Impact
The financial impact of this Office 365 security breach was devastating.
- Stolen Funds: Millions of dollars were stolen from multiple victim companies through fraudulent wire transfers.
- Loss of Investments: In some cases, the attackers manipulated investment decisions, resulting in significant financial losses.
- Reputational Damage: The breach caused considerable reputational damage to the affected companies, eroding investor confidence and damaging their brand image.
The long-term consequences extended beyond immediate financial losses, impacting future investment opportunities and business relationships.
Lessons Learned and Mitigation Strategies
This case study underscores the critical need for robust Office 365 security measures and proactive cybersecurity strategies.
Strengthening Office 365 Security
Implementing the following measures is crucial to mitigate the risk of similar breaches:
- Enable Multi-Factor Authentication (MFA): MFA is an absolute necessity, adding a crucial layer of security beyond passwords.
- Enforce Strong Password Policies: Implement strong password policies that require complex passwords and regular changes.
- Implement Advanced Threat Protection: Leverage Microsoft's advanced threat protection features to identify and block malicious emails and attachments.
- Utilize Email Filtering: Employ robust email filtering mechanisms to detect and quarantine suspicious emails before they reach users' inboxes.
- Conduct Regular Security Audits: Regular audits identify vulnerabilities before they can be exploited.
- Invest in Security Awareness Training: Educate employees on recognizing and reporting phishing attempts and other social engineering tactics.
The Importance of Proactive Security Measures
Proactive security measures are vital in identifying and mitigating risks before they are exploited.
- Penetration Testing: Simulate real-world attacks to identify vulnerabilities in your systems.
- Vulnerability Scanning: Regularly scan your systems for known vulnerabilities and promptly address any identified weaknesses.
- Security Awareness Training: Regularly train employees on cybersecurity best practices to reduce human error, a major factor in many breaches.
By proactively addressing potential vulnerabilities, organizations significantly reduce their risk of falling victim to similar attacks.
Conclusion
This case study of a multi-million dollar Office 365 security breach highlights the devastating consequences of neglecting robust cybersecurity measures. The attackers' sophisticated techniques underscore the need for a multi-layered approach to security, encompassing both technical safeguards and employee training. The financial impact, reputational damage, and long-term consequences emphasize the critical need for proactive security measures. Ignoring these vulnerabilities can lead to significant financial losses and irreparable reputational harm. Take immediate steps to strengthen your Office 365 security by implementing MFA, robust password policies, advanced threat protection, and comprehensive security awareness training. Don't wait for a breach to occur; proactively protect your organization and its valuable data. Explore Microsoft's security resources and consider engaging a cybersecurity professional to assess your current security posture and develop a comprehensive security plan. Protect yourself from the devastating impact of an Office 365 security breach.

Featured Posts
-
 Mangas Disaster Claim Leads To Drop In Japan Tourism Bookings
May 21, 2025
Mangas Disaster Claim Leads To Drop In Japan Tourism Bookings
May 21, 2025 -
 Nantes Et Ses Tours Un Defi Pour Les Cordistes
May 21, 2025
Nantes Et Ses Tours Un Defi Pour Les Cordistes
May 21, 2025 -
 Record Breaking Run William Goodge Conquers Australia On Foot
May 21, 2025
Record Breaking Run William Goodge Conquers Australia On Foot
May 21, 2025 -
 Trans Australia Run Record A New Attempt
May 21, 2025
Trans Australia Run Record A New Attempt
May 21, 2025 -
 Peppa Pigs New Baby Sister A Girl Arrives
May 21, 2025
Peppa Pigs New Baby Sister A Girl Arrives
May 21, 2025
Latest Posts
-
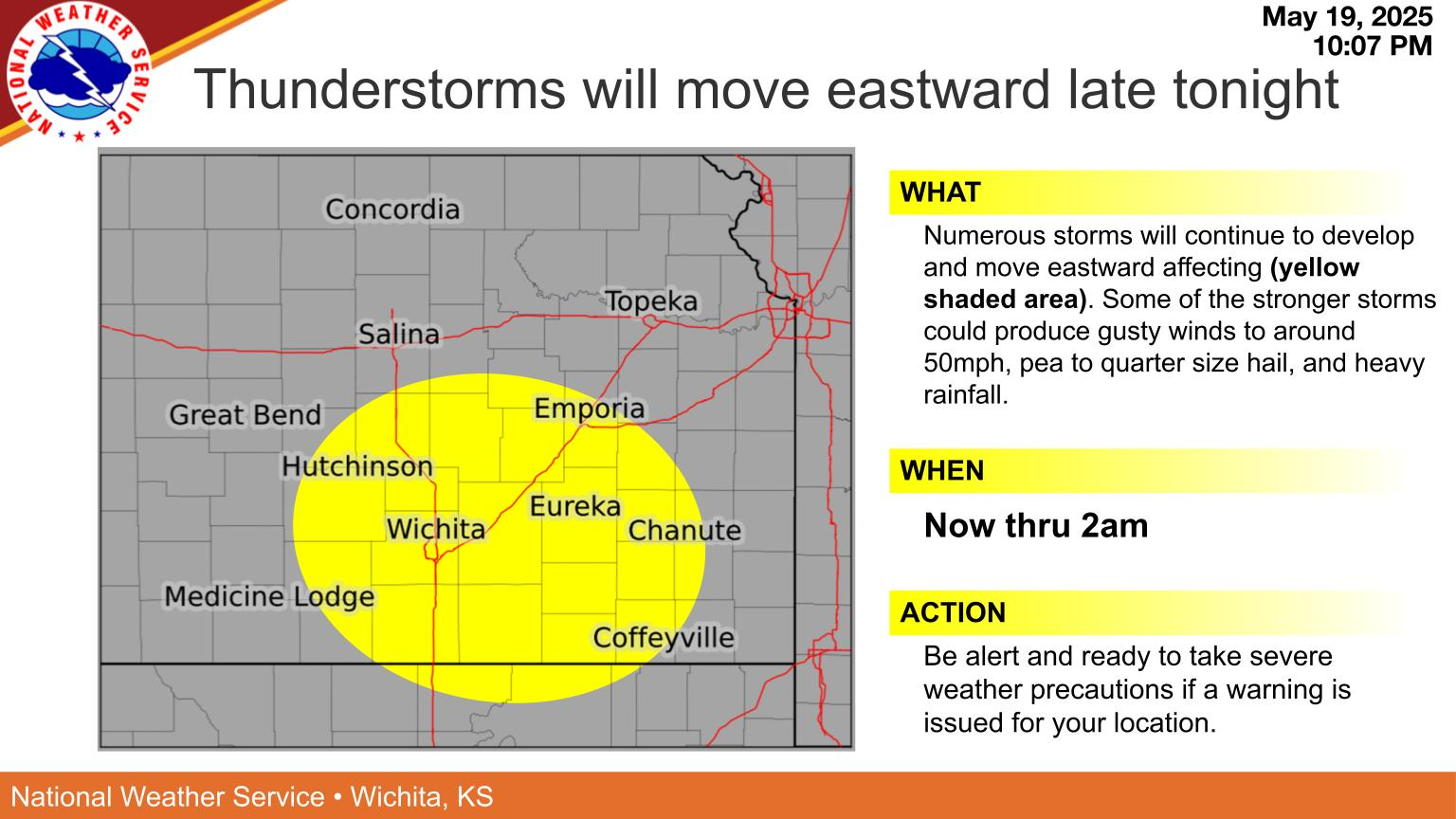 Storm Chance Overnight Severe Weather Potential Monday
May 21, 2025
Storm Chance Overnight Severe Weather Potential Monday
May 21, 2025 -
 Driving In A Wintry Mix Of Rain And Snow A Guide
May 21, 2025
Driving In A Wintry Mix Of Rain And Snow A Guide
May 21, 2025 -
 Understanding The Shift To Drier Weather Conditions
May 21, 2025
Understanding The Shift To Drier Weather Conditions
May 21, 2025 -
 Understanding And Coping With A Wintry Mix Of Rain And Snow
May 21, 2025
Understanding And Coping With A Wintry Mix Of Rain And Snow
May 21, 2025 -
 Drier Weather Ahead Tips For Home And Garden
May 21, 2025
Drier Weather Ahead Tips For Home And Garden
May 21, 2025
