Office365 Security Breach: Millions Stolen From Executive Inboxes
Table of Contents
The Anatomy of an Office365 Security Breach Targeting Executives
Executive email compromise (EBC) is a sophisticated form of cyberattack that specifically targets high-level employees within an organization. These attacks leverage the significant financial power and decision-making authority held by executives to maximize financial gain for cybercriminals. Several common attack vectors are used to breach Office365 security and gain access to executive inboxes:
- Phishing: Sophisticated phishing emails mimicking trusted sources (e.g., banks, payment processors, internal colleagues) are frequently used to trick executives into revealing login credentials or downloading malware. These emails often include urgent requests or sensitive information to pressure the recipient into immediate action.
- Malware: Malicious software, often delivered through infected attachments or links in phishing emails, can grant attackers access to the system and steal data, including login credentials and sensitive financial information. This malware can range from simple keyloggers to more complex ransomware and trojans.
- Compromised Credentials: Stolen login credentials, often obtained through previous data breaches on other platforms (credential stuffing), are used to directly access executive accounts. This method bypasses many traditional security measures.
- Zero-Day Exploits: Attackers exploit newly discovered vulnerabilities in Office365 applications or related software before patches are released. This requires sophisticated technical skills and is a particularly dangerous form of attack.
- Social Engineering: Attackers manipulate employees through various psychological tactics to gain access to information or systems. This could involve building trust with an employee to obtain their login credentials or manipulating them into clicking a malicious link.
The high value target: Executive accounts are highly sought after because they often have access to sensitive financial data, authorization for large transactions (like wire transfers), and the ability to initiate significant changes within the organization. This makes them prime targets for cybercriminals seeking substantial financial gain.
The Financial Impact of an Office365 Executive Email Compromise
The financial consequences of a successful Office365 security breach targeting executives can be catastrophic. Millions of dollars can be lost through a variety of methods:
- Loss of Funds: Direct theft of funds from company accounts through fraudulent wire transfers, unauthorized payments, and invoice manipulation is the most immediate and devastating impact.
- Reputational Damage: A data breach, especially one involving the compromise of executive accounts, severely damages an organization's reputation and erodes investor confidence. This can lead to lost business and decreased market value.
- Legal Fees and Regulatory Penalties: Organizations face hefty legal fees in responding to breaches and may incur significant penalties for non-compliance with data protection regulations (like GDPR or CCPA).
- Increased Insurance Premiums: After an Office365 security breach, insurance premiums for cyber liability coverage are likely to increase dramatically, adding to the overall financial burden.
The long-term consequences can include diminished customer trust, difficulties attracting and retaining talent, and a sustained negative impact on the organization's financial stability.
Strengthening Your Office365 Security: Practical Steps to Take
Protecting your organization from Office365 security breaches requires a multi-layered approach. Implementing robust security measures is crucial to mitigating the risk of executive email compromise.
Multi-Factor Authentication (MFA): MFA is arguably the single most important security measure you can implement. It adds an extra layer of security by requiring more than just a password to access accounts. Even if attackers obtain passwords through phishing or other means, they'll still be blocked without the second factor (like a code from an authenticator app).
- Implement MFA for all users: This should be mandatory, especially for executives and those with access to sensitive financial data.
- Regularly update software and patches: Keeping all software, including Office365 applications and operating systems, up-to-date with the latest security patches is essential to protect against known vulnerabilities.
- Employ advanced threat protection features: Office365 offers several advanced threat protection features, including anti-phishing and anti-malware capabilities, that should be fully utilized.
- Conduct regular security awareness training: Educating employees about phishing scams, social engineering tactics, and safe email practices is paramount in preventing attacks.
Advanced Security Measures: Consider implementing more advanced security solutions:
- Email Encryption: Encrypting sensitive emails ensures that only authorized recipients can access their content.
- Data Loss Prevention (DLP): DLP tools monitor and prevent the unauthorized transmission of sensitive data, helping to contain breaches.
- Advanced Threat Analytics: Utilize advanced analytics to identify suspicious activity and potential threats in real-time.
The Importance of Email Security Best Practices
Beyond technological solutions, robust email security best practices are critical:
- Phishing Awareness Training: Conduct regular and engaging phishing awareness training to educate employees on identifying and reporting suspicious emails. Simulate phishing attacks to test employee awareness.
- Strong Password Policies: Enforce strong password policies, including password complexity requirements and regular password changes. Encourage the use of password managers.
- Regular Monitoring: Regularly monitor user activity for unusual patterns or suspicious login attempts. Set up alerts for unusual access from unfamiliar locations or devices.
- Anti-Spam and Anti-Malware Solutions: Employ robust anti-spam and anti-malware solutions to filter out malicious emails and attachments before they reach users' inboxes. Regularly update these solutions to maintain effectiveness.
Conclusion
Office365 security breaches targeting executive inboxes pose a significant threat to organizations of all sizes, resulting in substantial financial losses and reputational damage. The consequences of an executive email compromise can be devastating, leading to millions of dollars stolen, legal battles, and a damaged reputation. However, by proactively implementing robust security measures, including multi-factor authentication, advanced threat protection, regular security awareness training, and strong email security best practices, organizations can significantly reduce their vulnerability. Don't wait until it's too late. Protect your organization from devastating Office365 security breaches. Invest in comprehensive Office365 security solutions today and safeguard your executive accounts – preventing millions from being stolen. Don't become another statistic.

Featured Posts
-
 Wwe Wrestle Mania 41 Memorial Day Weekend Ticket And Golden Belt Sale
May 23, 2025
Wwe Wrestle Mania 41 Memorial Day Weekend Ticket And Golden Belt Sale
May 23, 2025 -
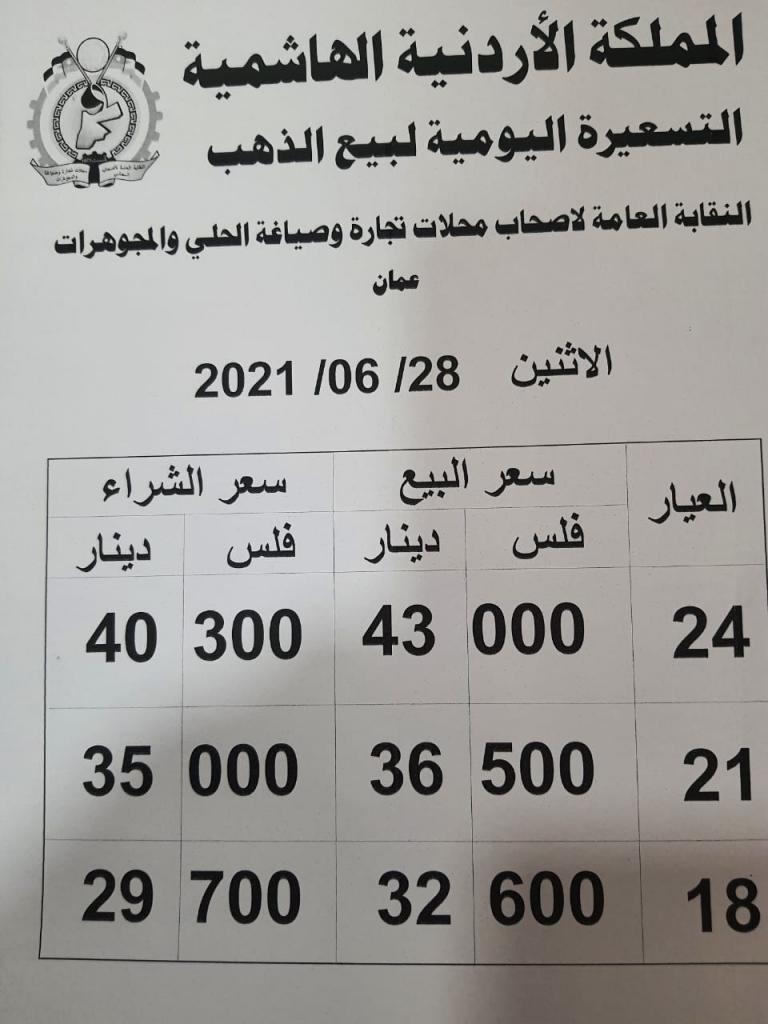 Mtabet Asear Aldhhb Fy Qtr Alithnyn 24 Mars
May 23, 2025
Mtabet Asear Aldhhb Fy Qtr Alithnyn 24 Mars
May 23, 2025 -
 Kermit The Frogs 2025 University Of Maryland Commencement Speech A Historic Event
May 23, 2025
Kermit The Frogs 2025 University Of Maryland Commencement Speech A Historic Event
May 23, 2025 -
 Joe Jonass Mature Reaction To A Couples Fight
May 23, 2025
Joe Jonass Mature Reaction To A Couples Fight
May 23, 2025 -
 Paradan Tasarruf Eden 3 Burc Kimler
May 23, 2025
Paradan Tasarruf Eden 3 Burc Kimler
May 23, 2025
Latest Posts
-
 Jonathan Groffs Asexuality A Candid Conversation
May 23, 2025
Jonathan Groffs Asexuality A Candid Conversation
May 23, 2025 -
 Jonathan Groff Discusses His Just In Time Role Honoring Bobby Darin And The Power Of Performance
May 23, 2025
Jonathan Groff Discusses His Just In Time Role Honoring Bobby Darin And The Power Of Performance
May 23, 2025 -
 Broadway Buzz Jonathan Groffs Immersive Bobby Darin Portrayal In Just In Time
May 23, 2025
Broadway Buzz Jonathan Groffs Immersive Bobby Darin Portrayal In Just In Time
May 23, 2025 -
 Jonathan Groffs Just In Time A Night Of Broadway Camaraderie
May 23, 2025
Jonathan Groffs Just In Time A Night Of Broadway Camaraderie
May 23, 2025 -
 Etoile A Spring Awakening Reunion Brings Laughter With Gideon Glick And Jonathan Groff
May 23, 2025
Etoile A Spring Awakening Reunion Brings Laughter With Gideon Glick And Jonathan Groff
May 23, 2025
