The Rise Of Post-Quantum Cryptography: Market Projections, Algorithmic Advancements, And Migration Strategies
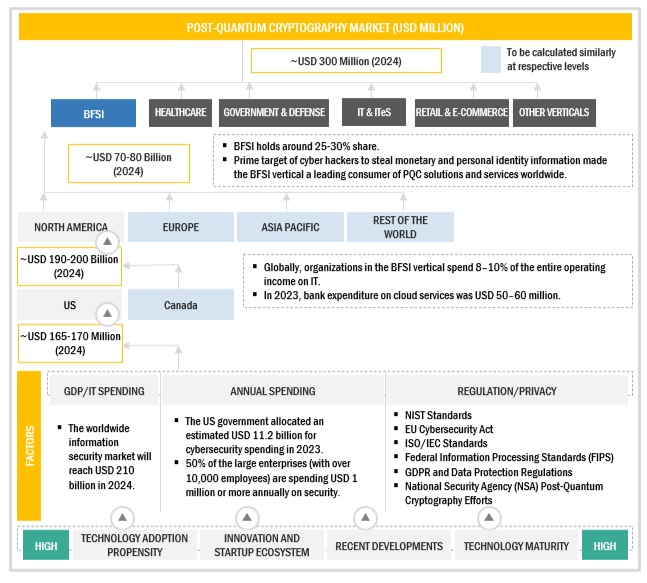
Table of Contents
Market Projections for Post-Quantum Cryptography
The post-quantum cryptography market is experiencing explosive growth, driven by the escalating threat of quantum computing and the increasing awareness of its potential to compromise existing security infrastructure. Market research firms predict a substantial Compound Annual Growth Rate (CAGR) over the coming years. This rapid expansion reflects the urgency with which organizations are seeking quantum-resistant cryptography solutions.
-
Key Market Drivers:
- Increasing quantum computing capabilities: Advances in quantum computing technology are bringing the threat of widespread decryption closer to reality, pushing the demand for PQC solutions.
- Rising cybersecurity threats: The increasing sophistication of cyberattacks necessitates a robust defense against both current and future threats, including those posed by quantum computers.
- Government regulations: Governments worldwide are starting to implement regulations and guidelines encouraging the adoption of post-quantum cryptographic techniques to safeguard national infrastructure and sensitive data.
-
Major Market Segments: The PQC market encompasses a range of segments, including:
- Software: This segment includes software libraries, development tools, and security applications integrating PQC algorithms.
- Hardware: Hardware-based solutions offering accelerated PQC implementations are crucial for high-performance applications.
- Services: Consulting, implementation, and managed security services related to PQC are gaining traction.
-
Market Statistics and Projections: Reports from Gartner and IDC project substantial growth, with the PQC market expected to reach billions of dollars in value within the next decade. Specific figures vary depending on the report and assumptions made, but the overall trend points to significant expansion across key geographic regions, including North America, Europe, and Asia-Pacific. These regions are driving market growth due to the high concentration of technology companies, robust cybersecurity infrastructure, and increasing government initiatives.
Keywords: Post-quantum cryptography market, PQC market size, PQC market growth, CAGR, cybersecurity market, quantum-resistant cryptography.
Algorithmic Advancements in Post-Quantum Cryptography
Several promising algorithmic approaches are at the forefront of post-quantum cryptography research and development. Each offers unique strengths and weaknesses, impacting its suitability for specific applications. The National Institute of Standards and Technology (NIST) has played a crucial role in standardizing these algorithms.
-
Lattice-based cryptography: This approach relies on the computational hardness of problems related to lattices in high-dimensional spaces. Examples include CRYSTALS-Kyber (key encapsulation mechanism) and CRYSTALS-Dilithium (digital signature algorithm), both selected by NIST for standardization.
-
Code-based cryptography: Building upon the difficulty of decoding random linear codes, this category offers strong security but typically involves larger key sizes and slower performance compared to other approaches. McEliece is a prominent example.
-
Multivariate cryptography: This method's security relies on the difficulty of solving systems of multivariate polynomial equations over finite fields. Rainbow is a well-known example.
-
Hash-based cryptography: Hash-based signatures offer excellent security but are fundamentally one-time signatures, necessitating key generation for each signature. SPHINCS+ is a notable example.
-
Isogeny-based cryptography: This relatively new approach utilizes the mathematical structure of isogenies between elliptic curves. SIKE (Supersingular Isogeny Key Encapsulation) is a significant example, although it recently faced security concerns and was subsequently dropped from consideration by NIST.
-
NIST Standardization: The NIST Post-Quantum Cryptography Standardization Project has been instrumental in evaluating and selecting quantum-resistant algorithms. Their selection process involved rigorous analysis, helping to establish a foundation for wider adoption.
Keywords: Lattice-based cryptography, code-based cryptography, multivariate cryptography, hash-based cryptography, isogeny-based cryptography, NIST PQC, quantum-resistant algorithms.
Challenges in Implementing Post-Quantum Cryptographic Algorithms
While PQC offers crucial security against quantum computers, implementing these algorithms presents several challenges:
-
Performance impact on existing systems: PQC algorithms often require more computational resources than current algorithms, potentially impacting the performance of existing systems, particularly in resource-constrained environments.
-
Increased key sizes: Many PQC algorithms require significantly larger key sizes than traditional algorithms, which impacts storage requirements and communication bandwidth.
-
Integration complexities with legacy systems: Integrating PQC into legacy systems can be complex and time-consuming, requiring careful planning and testing.
Keywords: PQC implementation challenges, key size, performance overhead, legacy system integration.
Migration Strategies for Post-Quantum Cryptography
Migrating to post-quantum cryptography requires a well-defined strategy to ensure a smooth and secure transition. A phased approach is highly recommended.
-
Assessment of current cryptographic infrastructure: Begin by thoroughly assessing your organization's current cryptographic infrastructure to identify all systems and applications that require protection against quantum attacks.
-
Selection of appropriate PQC algorithms: Based on the assessment, select appropriate PQC algorithms that meet your specific security needs and performance requirements, considering factors like key sizes, computational overhead, and algorithm maturity.
-
Pilot testing and implementation of chosen algorithms: Before a full-scale deployment, conduct thorough pilot testing to evaluate the performance and integration of selected algorithms within your environment.
-
Phased rollout and integration with existing systems: Implement PQC in a phased manner, starting with non-critical systems to minimize disruption and allow for adjustments as needed.
-
Ongoing monitoring and maintenance: Continuous monitoring and maintenance are essential to ensure the effectiveness and security of your PQC implementation.
-
Collaboration with cybersecurity experts: Partnering with cybersecurity experts experienced in PQC can significantly aid in the assessment, selection, and implementation of appropriate solutions.
Keywords: PQC migration strategy, cryptographic infrastructure assessment, algorithm selection, pilot testing, phased rollout, cybersecurity experts.
Conclusion
The rise of post-quantum cryptography is not just a technological trend; it's a critical necessity for ensuring long-term data security in the face of increasingly powerful quantum computers. Understanding market projections, algorithmic advancements, and effective migration strategies are paramount for businesses and organizations seeking to protect their sensitive information. Don't wait for a quantum computing threat to materialize—begin your transition to post-quantum cryptography today. Invest time in researching the best PQC solutions and develop a robust migration plan to safeguard your digital assets against future quantum attacks. Learn more about securing your future with post-quantum cryptography now!

Featured Posts
-
 Chris And Meg A Wild Summer
May 13, 2025
Chris And Meg A Wild Summer
May 13, 2025 -
 Ostapenko Stuns Swiatek Again Reaches Stuttgart Semifinals
May 13, 2025
Ostapenko Stuns Swiatek Again Reaches Stuttgart Semifinals
May 13, 2025 -
 School Stabbing Victim Remembered At Funeral Service
May 13, 2025
School Stabbing Victim Remembered At Funeral Service
May 13, 2025 -
 Protecting Uks Rarest Animals From The Growing Threat Of Wildfires
May 13, 2025
Protecting Uks Rarest Animals From The Growing Threat Of Wildfires
May 13, 2025 -
 Oregon Ducks Womens Basketball Overtime Victory Against Vanderbilt
May 13, 2025
Oregon Ducks Womens Basketball Overtime Victory Against Vanderbilt
May 13, 2025
Latest Posts
-
 Leonardo Di Caprios Unexpected Met Gala Date Vittoria Ceretti
May 13, 2025
Leonardo Di Caprios Unexpected Met Gala Date Vittoria Ceretti
May 13, 2025 -
 Finding Eva Longorias Searching For Spain A Viewing Guide
May 13, 2025
Finding Eva Longorias Searching For Spain A Viewing Guide
May 13, 2025 -
 Leonardo Di Caprio And Vittoria Cerettis Surprise Met Gala Appearance
May 13, 2025
Leonardo Di Caprio And Vittoria Cerettis Surprise Met Gala Appearance
May 13, 2025 -
 Watch Eva Longoria Searching For Spain Streaming Guide
May 13, 2025
Watch Eva Longoria Searching For Spain Streaming Guide
May 13, 2025 -
 Where To Stream Eva Longorias Searching For Spain
May 13, 2025
Where To Stream Eva Longorias Searching For Spain
May 13, 2025
