Millions Made From Exec Office365 Hacks, Federal Investigation Reveals
Table of Contents
The Modus Operandi of the Office365 Hacks
The cybercriminals behind this operation employed a multi-pronged approach, leveraging several techniques to gain access to high-value executive accounts within Microsoft Office 365 environments.
Phishing and Spear Phishing Attacks
The primary method of attack involved highly targeted phishing and spear phishing campaigns. These malicious emails were meticulously crafted to appear legitimate, often impersonating trusted individuals or organizations to bypass suspicion.
- Examples of phishing emails: Emails mimicking internal communications, invoices from known vendors, or urgent requests from supposed executives.
- Use of CEO fraud: Hackers impersonated CEOs or other high-ranking officials to instruct employees to perform actions like initiating wire transfers or providing sensitive information.
- Impersonation of trusted individuals: Emails appeared to come from colleagues, IT support, or external partners, creating a sense of urgency and trust.
These attacks often exploited vulnerabilities in Microsoft Office 365's multi-factor authentication (MFA) or its absence. Bypassing MFA, often through social engineering, was key to their success.
Exploiting Weak Passwords and Security Gaps
Beyond sophisticated social engineering, the hackers exploited common vulnerabilities within Office 365 systems and user accounts.
- Weak passwords: Many executive accounts used easily guessable or reused passwords, making them vulnerable to brute-force attacks or credential stuffing.
- Lack of MFA: The absence of multi-factor authentication significantly weakened security, making it easier for attackers to gain access even with compromised credentials.
- Compromised credentials: Stolen credentials, obtained through phishing or other means, were leveraged to access multiple accounts.
- Unpatched software: Outdated software and unpatched vulnerabilities provided entry points for malicious code and malware.
Credential stuffing attacks, where stolen credentials from one system are used to attempt logins on other platforms, played a significant role in the breaches. Strong password policies and the mandatory implementation of multi-factor authentication are critical defenses against such attacks.
Post-Compromise Activities
Once inside the Office365 environment, the hackers engaged in a range of malicious activities to maximize their gains.
- Data theft: Sensitive company data, including financial records, intellectual property, and customer information, was exfiltrated.
- Financial fraud: Funds were illicitly transferred through compromised accounts, often using wire transfer fraud schemes.
- Account takeover: Complete control of executive accounts allowed for further manipulation and unauthorized actions.
- Ransomware deployment: In some cases, ransomware was deployed to encrypt data and demand ransom payments.
Attackers used lateral movement techniques, moving from one compromised account to another within the organization's network, widening their access and impact.
The Scale of the Financial Losses and Impact
The Office365 hacks resulted in substantial financial losses and far-reaching consequences.
Monetary Damage
The investigation revealed millions of dollars were stolen across numerous victims. While precise figures remain undisclosed for some cases, the average loss per victim is substantial, impacting both large corporations and smaller businesses significantly.
- Total amount stolen: Millions of dollars, the exact figure is still being compiled.
- Average loss per victim: Varying, but often representing a considerable financial blow.
- Industries most affected: The finance, healthcare, and technology sectors were particularly targeted.
The long-term economic impact on affected businesses can include lost revenue, increased operational costs, and damaged investor confidence.
Reputational Damage and Loss of Customer Trust
Beyond the direct financial losses, the data breaches caused significant reputational damage and eroded customer trust.
- Damage to brand reputation: Public disclosure of a security breach can severely tarnish an organization's image.
- Loss of customer confidence: Customers may be hesitant to do business with companies perceived as having weak security.
- Legal liabilities: Data breaches can lead to significant legal and regulatory fines.
The ripple effects can extend far beyond the immediate victims, impacting investor confidence and long-term business viability.
The Victims
The hacking ring targeted a broad spectrum of organizations and individuals.
- Large corporations: Major corporations with valuable intellectual property and financial resources were prime targets.
- Small businesses: Smaller businesses, often lacking robust security infrastructure, were also vulnerable.
- High-net-worth individuals: Executive accounts were targeted for their access to funds and sensitive information.
The wide-ranging impact underscores the indiscriminate nature of these attacks and the need for comprehensive cybersecurity measures regardless of organization size.
The Federal Investigation and its Findings
The federal investigation involved a collaborative effort to unravel the complex cybercrime ring.
The Investigation Process
Federal agencies employed various methods to trace the activities of the hackers.
- Tracing financial transactions: Investigators meticulously tracked the flow of stolen funds to identify the perpetrators and their networks.
- Identifying the perpetrators: Law enforcement utilized digital forensics and intelligence gathering to locate and identify the individuals responsible.
- Seizing assets: Assets obtained through the illegal activities were seized to compensate victims and disrupt the criminal enterprise.
The investigation involved several federal agencies specializing in cybercrime investigation and financial fraud.
Arrests and Charges
The investigation culminated in several arrests and criminal charges.
- Number of arrests: The exact number of arrests is subject to ongoing investigations and legal proceedings.
- Charges filed: Charges included wire fraud, conspiracy to commit wire fraud, and identity theft.
- Potential sentences: Those convicted face significant prison sentences and substantial fines.
While some arrests have been made, the investigation continues to uncover further details and potential accomplices.
Lessons Learned and Future Implications
The Office365 hacks serve as a stark reminder of the evolving nature of cybercrime and the critical need for proactive cybersecurity measures.
- Importance of cybersecurity awareness training: Regular training for all employees is essential to mitigate phishing and social engineering risks.
- Stronger password policies: Enforcing complex and unique passwords, combined with regular password changes, is critical.
- Enhanced MFA: Implementing robust multi-factor authentication is a non-negotiable security requirement.
- Regular software updates: Keeping software and systems updated with the latest security patches is paramount.
- Incident response planning: Having a well-defined incident response plan is crucial for minimizing the impact of a breach.
The need for collaboration between businesses and law enforcement agencies to combat cybercrime effectively is paramount.
Conclusion
The federal investigation into the millions lost through executive Office365 hacks underscores the critical need for robust cybersecurity practices. The sophisticated nature of these attacks emphasizes the importance of proactive measures such as strong password policies, multi-factor authentication, regular security awareness training, and robust incident response plans to address any potential Office365 security breaches. Businesses and individuals must remain vigilant against evolving cyber threats and invest in comprehensive cybersecurity solutions to protect themselves from costly Office365 hacks and other forms of cybercrime. Don't wait until it's too late—protect your Office365 accounts today.

Featured Posts
-
 The Uks Eurovision 2025 Result 19th Place What Went Wrong
May 19, 2025
The Uks Eurovision 2025 Result 19th Place What Went Wrong
May 19, 2025 -
 The Impact Of Music Festivals On London Parks Mark Rylances View
May 19, 2025
The Impact Of Music Festivals On London Parks Mark Rylances View
May 19, 2025 -
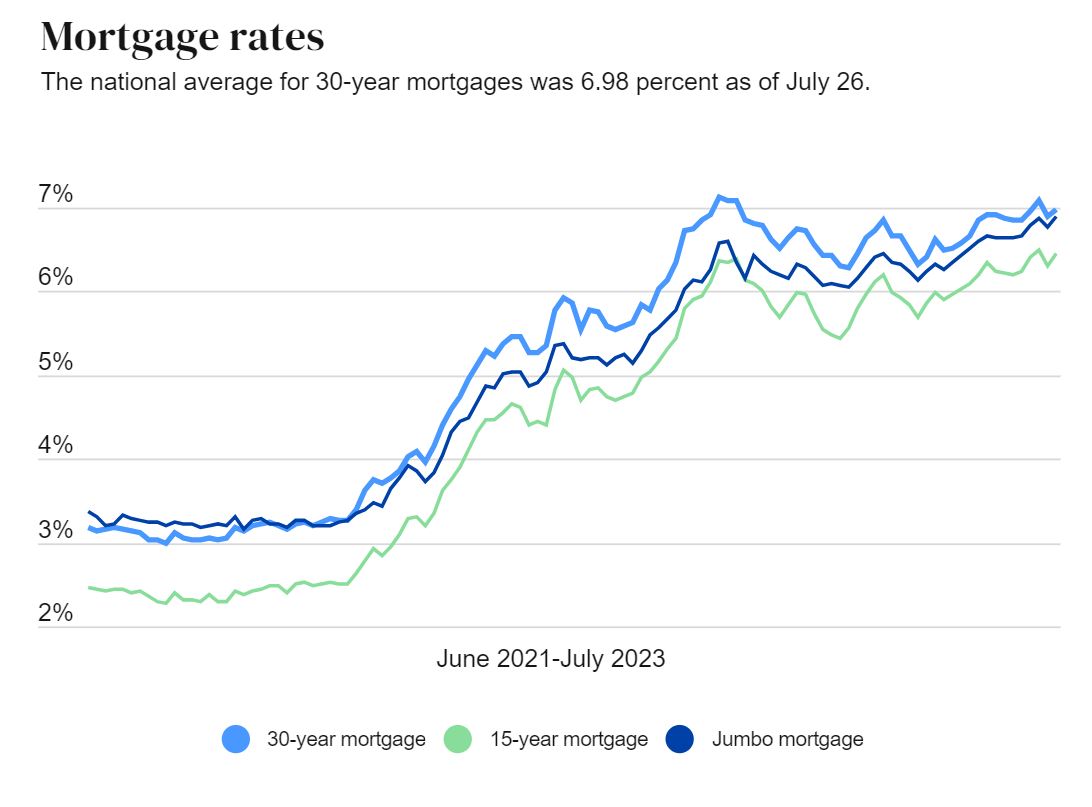 Federal Debt Crisis Implications For The Housing Market And Mortgage Rates
May 19, 2025
Federal Debt Crisis Implications For The Housing Market And Mortgage Rates
May 19, 2025 -
 The End Of Mississippi Income Tax What Does It Mean For Hernando
May 19, 2025
The End Of Mississippi Income Tax What Does It Mean For Hernando
May 19, 2025 -
 The Trump Era And Aerospace A Review Of Announced Deals And Their Impact
May 19, 2025
The Trump Era And Aerospace A Review Of Announced Deals And Their Impact
May 19, 2025
