Block Mirror: Bypassing Censorship And Accessing Blocked Content
Table of Contents
Understanding Block Mirrors and How They Work
A block mirror, in simple terms, is a mirrored website or server located outside the censored region. It acts as a proxy, providing an alternative route to access content blocked within a specific geographical area or by a network firewall. Instead of connecting directly to the censored website, your request is routed through the block mirror, which then retrieves the content and forwards it to you. This circumvents the restrictions imposed by the censoring entity.
-
Uses a different IP address: By using a server with an IP address outside the restricted area, a block mirror masks your location, making it appear as though you are accessing the content from an unrestricted location. This is crucial for bypassing geographical restrictions imposed by streaming services, social media platforms, and other online services.
-
Often employs encryption protocols like HTTPS: Many reliable block mirrors utilize HTTPS encryption to secure the communication between your device and the mirror server. This protects your data from interception and ensures privacy during transmission. However, not all block mirrors prioritize security, so due diligence is crucial.
-
Can be implemented through various technologies: The technology behind block mirrors varies. They can leverage VPNs (Virtual Private Networks), proxies, or even the Tor network to achieve their goal of circumventing censorship. Each method offers a different level of security and anonymity.
-
Provides an alternative path: Block mirrors effectively create a bypass around firewalls and censorship filters that actively block access to specific websites or content. This allows users to access information that would otherwise be unavailable.
Benefits of Using a Block Mirror
Accessing Censored Information
Block mirrors are invaluable for accessing websites, applications, and content blocked by governments, organizations, or internet service providers. This includes a wide range of content frequently targeted by censorship:
-
Access to news and information from various perspectives: In regions with strict media control, block mirrors can provide access to news sources and information that offer diverse viewpoints, countering state-controlled narratives.
-
Unrestricted access to social media platforms: Many countries restrict access to popular social media platforms like Facebook, Twitter, and Instagram. Block mirrors offer a way to bypass these restrictions and connect with global communities.
-
Ability to use blocked applications and services: Certain applications and online services might be blocked in specific regions. Block mirrors can provide access to these services, enabling users to utilize them as intended.
-
Bypassing regional restrictions on streaming services: Streaming services often impose geographical limitations on their content libraries. Block mirrors can help circumvent these restrictions, giving users access to a wider selection of movies, TV shows, and other streaming content.
Enhanced Online Privacy and Security
While not a primary function, using a block mirror can indirectly improve your online privacy and security. This improvement is dependent on the implementation and security measures of the specific block mirror being used.
-
Masking IP address: The block mirror hides your real IP address, protecting your online identity and making it harder to track your online activities.
-
Potential encryption for secure data transmission: Many block mirrors utilize HTTPS encryption, protecting your data from unauthorized access during transmission. However, this is not a guarantee, and users should verify the security protocols of the block mirror before use.
-
Circumventing tracking and surveillance: By masking your IP address and routing your traffic through a different server, you make it more difficult for entities to track your online behavior and collect your data.
Risks and Limitations of Using Block Mirrors
Security Concerns
While block mirrors offer benefits, it's crucial to acknowledge the potential security risks involved:
-
Risk of malware and phishing attacks: Malicious actors can set up fake block mirrors designed to infect your devices with malware or steal your personal information through phishing scams.
-
Vulnerability to data interception: If the block mirror itself is insecure or poorly implemented, your data may be vulnerable to interception. This highlights the importance of choosing reliable and reputable block mirror providers.
-
Importance of verifying mirror authenticity and security: Before using any block mirror, it’s essential to verify its authenticity and security. Look for HTTPS encryption, positive user reviews, and established providers with a proven track record.
Performance Issues
Using a block mirror can impact your internet experience:
-
Slower loading times: Routing your traffic through a remote server can lead to increased loading times compared to direct access.
-
Increased latency: The geographical distance between you and the block mirror server can introduce latency, resulting in delays and slower response times.
-
Potential for connectivity problems: Depending on network conditions and the block mirror's infrastructure, you may experience connectivity issues, such as dropped connections or intermittent access.
Legal and Ethical Implications
The legal and ethical implications of using block mirrors vary depending on your jurisdiction and the content being accessed:
-
Legality depends on jurisdiction and accessed content: Accessing blocked content may violate local laws in some regions. It is crucial to understand the legal landscape in your location before using a block mirror.
-
Ethical considerations related to accessing copyrighted material: Using a block mirror to access copyrighted material without permission is unethical and potentially illegal.
-
Potential for misuse in illegal activities: Block mirrors can be misused for illegal activities. Responsible and ethical use is paramount.
Conclusion
Block mirrors offer a valuable solution for bypassing censorship and accessing blocked content. They provide access to information and services otherwise unavailable, but it's crucial to understand their limitations and associated risks. Always prioritize secure and reliable block mirror services to mitigate potential security threats. If you're seeking unrestricted access to the internet, understanding how to effectively use a block mirror is a valuable skill, but remember to do so responsibly and within the bounds of the law. Research the different options available, prioritize your online security, and make informed choices regarding your access to information. Choose your block mirror wisely and be aware of the potential pitfalls.

Featured Posts
-
 Dreigende Actie Tegen Npo Directeur Frederieke Leeflang
May 15, 2025
Dreigende Actie Tegen Npo Directeur Frederieke Leeflang
May 15, 2025 -
 Chandler Simpsons Breakout Game Rays Complete Padres Sweep
May 15, 2025
Chandler Simpsons Breakout Game Rays Complete Padres Sweep
May 15, 2025 -
 Finding The Right Black Decker Steam Iron A Detailed Guide
May 15, 2025
Finding The Right Black Decker Steam Iron A Detailed Guide
May 15, 2025 -
 Jimmy Butler Vs Kevin Durant What The Warriors Really Need
May 15, 2025
Jimmy Butler Vs Kevin Durant What The Warriors Really Need
May 15, 2025 -
 The Mavs Losses Comparing The Impact Of Jalen Brunsons Departure And The Luka Doncic Trade
May 15, 2025
The Mavs Losses Comparing The Impact Of Jalen Brunsons Departure And The Luka Doncic Trade
May 15, 2025
Latest Posts
-
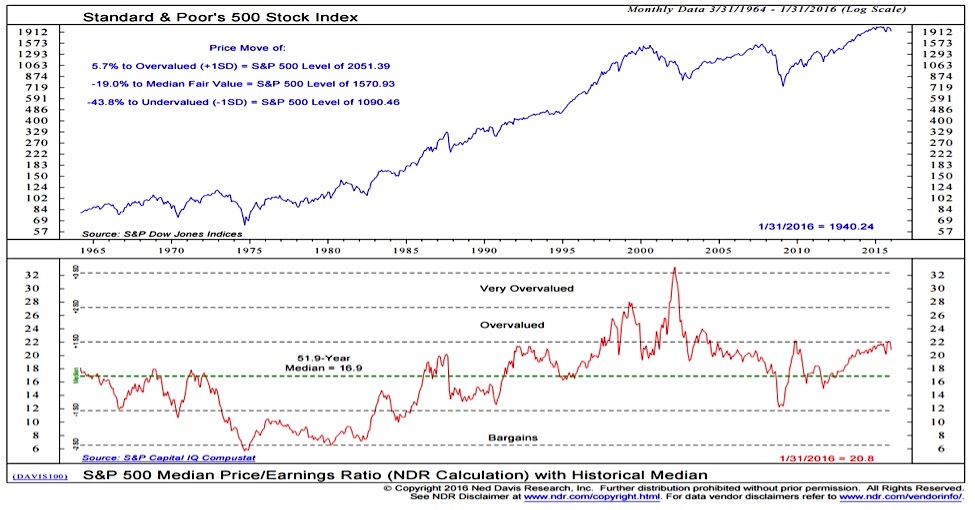 Addressing Concerns Bof As Perspective On Elevated Stock Market Valuations
May 16, 2025
Addressing Concerns Bof As Perspective On Elevated Stock Market Valuations
May 16, 2025 -
 Evaluating The Economic Impact Of Trumps Tariffs On California Revenue 16 Billion
May 16, 2025
Evaluating The Economic Impact Of Trumps Tariffs On California Revenue 16 Billion
May 16, 2025 -
 Behind The Scenes Xis Team And The Us Deal
May 16, 2025
Behind The Scenes Xis Team And The Us Deal
May 16, 2025 -
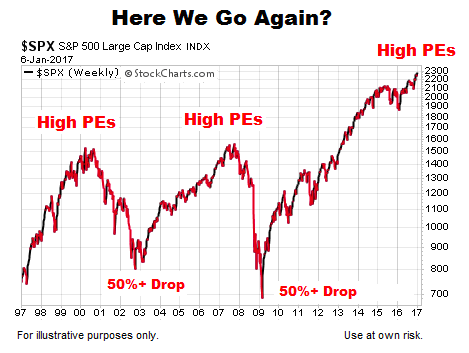 Bof As View Why High Stock Market Valuations Are Justified
May 16, 2025
Bof As View Why High Stock Market Valuations Are Justified
May 16, 2025 -
 Assessing The Damage Trump Tariffs And Californias Projected 16 Billion Revenue Decline
May 16, 2025
Assessing The Damage Trump Tariffs And Californias Projected 16 Billion Revenue Decline
May 16, 2025
