The Future Of Block Mirrors: Innovation And The Fight Against Censorship
Table of Contents
The Growing Need for Block Mirrors
The Rise of Censorship
Governments and corporations worldwide are increasingly employing censorship to control information flow. Methods range from outright website blocking and content removal to more sophisticated techniques like deep packet inspection and internet shutdowns. This stifles free speech and limits access to vital information.
- Examples of censorship: The Great Firewall of China, restrictions on social media in various countries, the blocking of news websites in authoritarian regimes.
- Specific examples of censored content: Political dissent, journalistic investigations, information about human rights abuses, and access to alternative viewpoints.
- Impact of censorship: Limits on freedom of expression, hindering democratic processes, restricting access to education and healthcare information, and fueling misinformation.
Block Mirrors as a Solution
Block mirrors offer a powerful countermeasure to censorship by providing alternative access points to blocked content. They work by creating multiple copies of websites or data and distributing them across a network, making it difficult for censors to block all access points.
- Different types of block mirrors: Distributed networks like BitTorrent, decentralized storage systems using IPFS (InterPlanetary File System), and peer-to-peer (P2P) mirroring techniques.
- Technical aspects: These systems use mirroring techniques to replicate content across multiple servers, redirecting users to unblocked mirrors via various methods, including domain name system (DNS) manipulation and proxy servers.
- Advantages of using block mirrors: Increased resilience to censorship, improved website availability, enhanced user privacy, and protection against data loss.
Technological Advancements in Block Mirror Technology
Decentralized Storage and Blockchain
Decentralized storage solutions, such as IPFS, and blockchain technology are revolutionizing block mirror technology, creating more resilient and censorship-resistant systems.
- Advantages of decentralized storage: Data is distributed across many nodes, making it highly resistant to single points of failure or censorship attacks. Improved data availability and redundancy.
- How blockchain improves transparency and security: Blockchain provides a transparent and immutable record of data, making it harder to tamper with or censor. It enhances security through cryptographic techniques.
- Examples of projects: Several projects are exploring the integration of blockchain and IPFS for creating censorship-resistant data storage and distribution networks.
AI and Machine Learning for Enhanced Security
AI and machine learning are increasingly vital for improving the security and effectiveness of block mirrors. They can help detect and adapt to new censorship techniques.
- Examples of AI-powered security measures: AI can identify and mitigate DDoS attacks, detect patterns of censorship, and automatically redirect users to unblocked mirrors.
- The role of machine learning in predicting censorship attempts: Machine learning algorithms can analyze data to predict censorship attempts and proactively adjust the block mirror network to avoid disruptions.
- Challenges in developing robust AI-based solutions: The constant evolution of censorship techniques requires ongoing development and adaptation of AI models. Data privacy concerns also need careful consideration.
Challenges and Limitations of Block Mirrors
Legal and Ethical Considerations
The use of block mirrors raises important legal and ethical considerations.
- Legal frameworks surrounding online content and censorship: Laws vary widely across jurisdictions regarding online content and censorship, making it difficult to determine the legality of using block mirrors in all situations.
- Ethical considerations for distributing potentially illegal or harmful content: Block mirrors could potentially be used to distribute illegal or harmful content. Responsible disclosure and content moderation strategies are crucial.
- The role of responsible disclosure: Transparency and responsible disclosure are essential to mitigate potential misuse of block mirror technology.
Technical Vulnerabilities and Attack Vectors
Block mirrors are not immune to attacks.
- Common attacks against block mirrors: Distributed denial-of-service (DDoS) attacks, attempts to identify and block mirror servers, and sophisticated censorship techniques aimed at disrupting the network.
- Methods for improving the resilience and security of block mirrors: Employing robust security measures, utilizing decentralized architectures, and continuously monitoring and updating the system to adapt to new threats.
- The ongoing arms race between censorship and circumvention technologies: The development of block mirrors is an ongoing effort to stay ahead of increasingly sophisticated censorship techniques.
The Future Landscape of Block Mirrors
Integration with VPNs and other Privacy Tools
The synergy between block mirrors and other privacy-enhancing tools like VPNs and Tor enhances censorship resistance significantly.
- Benefits of combining block mirrors with VPNs and Tor: VPNs mask the user's IP address, while Tor anonymizes network traffic, further hindering censorship efforts. Combined with block mirrors, this creates a robust system for accessing blocked content.
- The future development of integrated privacy solutions: Future development will focus on creating seamless integration between these technologies for enhanced user privacy and security.
The Role of User Communities and Collaboration
User participation and collaboration are crucial for the success of block mirrors.
- The role of open-source software and community involvement: Open-source development fosters transparency, community scrutiny, and collective improvement of the technology.
- The creation of decentralized governance models: Decentralized governance models ensure that no single entity controls the block mirror network, increasing its resilience and preventing censorship.
- The importance of user education and awareness: Educating users about the benefits and risks of block mirrors is essential for their effective use.
Conclusion
The future of block mirrors is intertwined with the ongoing fight for online freedom. As censorship tactics become more sophisticated, innovation in block mirror technology must keep pace. By leveraging advancements in decentralized storage, AI, and user collaboration, we can build a more resilient and accessible internet, ensuring that information remains freely available for all. To learn more about the latest developments and contribute to this crucial effort, research and explore the world of block mirrors and related technologies. Join the movement to protect online freedom and support the development of innovative solutions like block mirror networks and decentralized information access tools.
Featured Posts
-
 Q2 2026
May 15, 2025
Q2 2026
May 15, 2025 -
 Anthony Edwards Vulgar Comment Costs Him 50 000 Nba Fine
May 15, 2025
Anthony Edwards Vulgar Comment Costs Him 50 000 Nba Fine
May 15, 2025 -
 Nba Playoffs Knicks Brunson Injury Update And Pistons Showdown
May 15, 2025
Nba Playoffs Knicks Brunson Injury Update And Pistons Showdown
May 15, 2025 -
 Athletic Club De Bilbao Match Reports Team News And More On Vavel Usa
May 15, 2025
Athletic Club De Bilbao Match Reports Team News And More On Vavel Usa
May 15, 2025 -
 Anthony Edwards Baby Mama Drama Ignites Twitter
May 15, 2025
Anthony Edwards Baby Mama Drama Ignites Twitter
May 15, 2025
Latest Posts
-
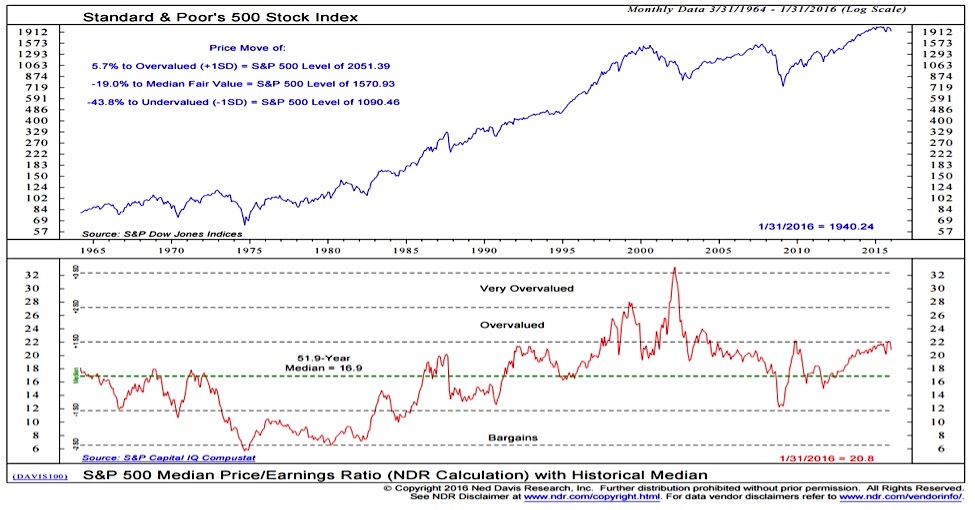 Addressing Concerns Bof As Perspective On Elevated Stock Market Valuations
May 16, 2025
Addressing Concerns Bof As Perspective On Elevated Stock Market Valuations
May 16, 2025 -
 Evaluating The Economic Impact Of Trumps Tariffs On California Revenue 16 Billion
May 16, 2025
Evaluating The Economic Impact Of Trumps Tariffs On California Revenue 16 Billion
May 16, 2025 -
 Behind The Scenes Xis Team And The Us Deal
May 16, 2025
Behind The Scenes Xis Team And The Us Deal
May 16, 2025 -
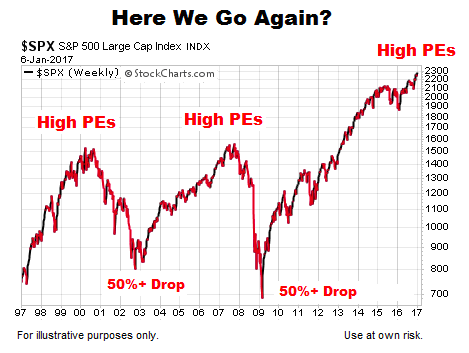 Bof As View Why High Stock Market Valuations Are Justified
May 16, 2025
Bof As View Why High Stock Market Valuations Are Justified
May 16, 2025 -
 Assessing The Damage Trump Tariffs And Californias Projected 16 Billion Revenue Decline
May 16, 2025
Assessing The Damage Trump Tariffs And Californias Projected 16 Billion Revenue Decline
May 16, 2025
